This is the write up for the room Hashing – Crypto 101 on Tryhackme and it is part of the complete beginners path
Make connection with VPN or use the attackbox on Tryhackme site to connect to the Tryhackme lab environment.
Tasks Hashing – Crypto 101
Task 1
Read all that is in the task and press complete
Task 2
2.1 What is the output size in bytes of the MD5 hash function?
Answer: 16
2.2 Can you avoid hash collisions? (Yea/Nay)
Answer: Nay
2.3 If you have an 8 bit hash output, how many possible hashes are there?
Took me a while to understand this. But here is a good explenation Hash Functions (nakamoto.com)
2 to the power of 8 = 256
Answer: 256
Task 3
3.1 Crack the hash “d0199f51d2728db6011945145a1b607a” using the rainbow table manually.
Go to Hash Type Identifier – Identify unknown hashes and put in the hash. The password will reveal itself
3.2 Crack the hash “5b31f93c09ad1d065c0491b764d04933” using online tools
Go to Hash Type Identifier – Identify unknown hashes and put in the hash. The password will reveal itself
3.3 Should you encrypt passwords? Yea/Nay
Answer: Nay
Task 4:
4.1 How many rounds does sha512crypt ($6$) use by default?
With a little bit of google I came accross this site that hold the answer Hashing passwords: SHA-512 can be stronger than bcrypt (by doing more rounds) – Michael Franzl
Answer ; 5000
4.2 What’s the hashcat example hash (from the website) for Citrix Netscaler hashes?
Open the example site from the text in the task example_hashes [hashcat wiki]. Look for the Citrix Netscaler. There are 2. The answer is the one that is not 512
4.3 How long is a Windows NTLM hash, in characters?
You can find the answer here example_hashes [hashcat wiki].
Answer 32
Task 5
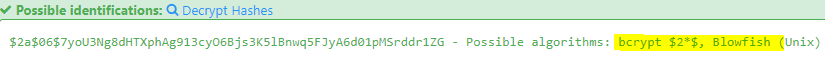
5.1 Crack this hash: $2a$06$7yoU3Ng8dHTXphAg913cyO6Bjs3K5lBnwq5FJyA6d01pMSrddr1ZG
First we need to identify the hash by going to Hash Type Identifier – Identify unknown hashes
Now we need to find the right module for hashcat to use. Type in
hashcat -h | grep -iF "bcrypt"
We now know it is module 3200. Now let’s crack it by typing in
hashcat -m 3200 '$2a$06$7yoU3Ng8dHTXphAg913cyO6Bjs3K5lBnwq5FJyA6d01pMSrddr1ZG' /usr/share/wordlists/rockyou.txt
5.2 Crack this hash: 9eb7ee7f551d2f0ac684981bd1f1e2fa4a37590199636753efe614d4db30e8e1
First we need to identify the hash by going to Hash Type Identifier – Identify unknown hashes
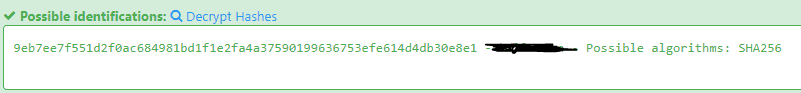
And it already giving the password
5.3 Crack this hash: $6$GQXVvW4EuM$ehD6jWiMsfNorxy5SINsgdlxmAEl3.yif0/c3NqzGLa0P.S7KRDYjycw5bnYkF5ZtB8wQy8KnskuWQS3Yr1wQ0
First we need to identify the hash by going to Hash Type Identifier – Identify unknown hashes
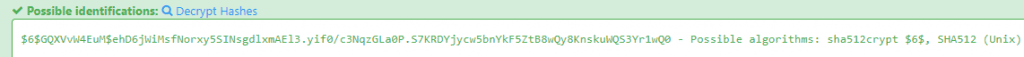
Now we know it is sha512crypt we need to fin the correct module by typing in
hashcat -h | grep -iF "sha512crypt"
The module is 1800 . Now let’s start cracking by typing in
hashcat -m 1800 '$6$GQXVvW4EuM$ehD6jWiMsfNorxy5SINsgdlxmAEl3.yif0/c3NqzGLa0P.S7KRDYjycw5bnYkF5ZtB8wQy8KnskuWQS3Yr1wQ0' /usr/share/wordlists/rockyou.txt
The answer will reveal itself once hashcat is done
5.4 Bored of this yet? Crack this hash: b6b0d451bbf6fed658659a9e7e5598fe
First we need to identify the hash by going to Hash Type Identifier – Identify unknown hashes
and once we put in the hash the password is there as well. So no cracking needed