This is the write up for the room Sysinternals on Tryhackme and it is part of the Tryhackme Cyber Defense Path
Make connection with VPN or use the attack box on Tryhackme site to connect to the Tryhackme lab environment
TASK Sysinternals
Task 1
Start the machine attached to this task then read all that is in this task. Use the tool Remina to connect with an RDP session to the Machine.
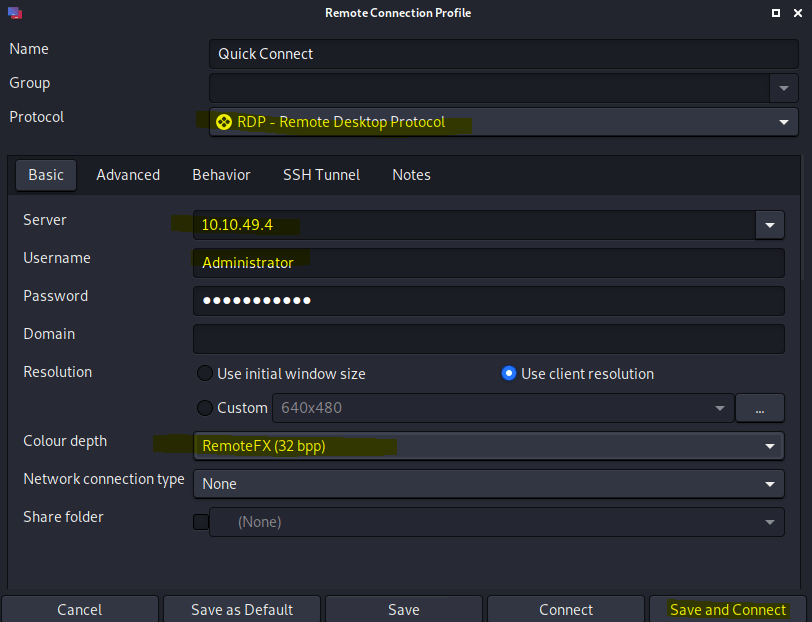
When asked to accept the certificate press yes
1.1 When did Microsoft acquire the Sysinternals tools?
Answer: 2005
Task 2
Read all that is in this task and make not of the download URL https://docs.microsoft.com/en-us/sysinternals/downloads/
The Sysinternal tools are already installed on the VM. Under c:\tools\sysint
2.1 What is the last tool listed within the Sysinternals Suite?
open the download URL and scroll all the way down to the last tool
Answer: zoomit
Task 3
Open a Privledge CMD and type in the following commands
powershell
get-service webclient
start-service webclient
get-service webclient
Control.exe /name Microsoft.NetworkAndSharingCenter
Change advanced sharing setting and select Turn on network discovery
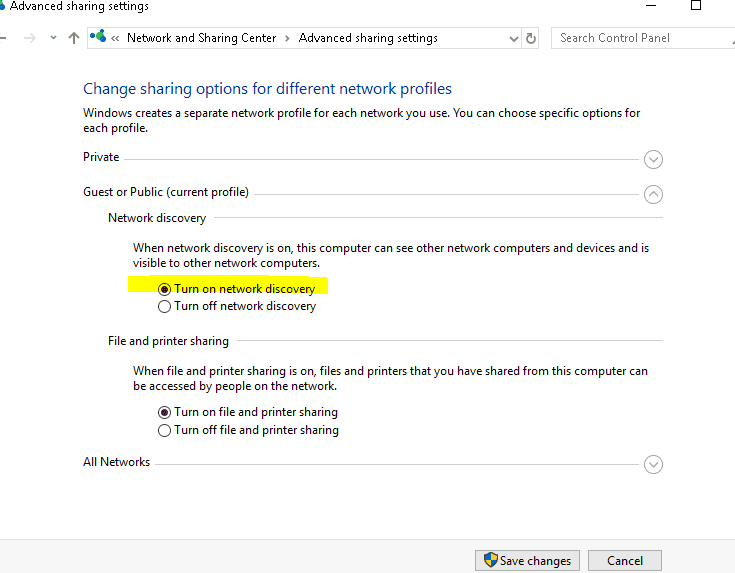
You can now run the tools directly from \\live.sysinternals.com\tools\
3.1 What service needs to be enabled on the local host to interact with live.sysinternals.com?
Answer: Webclient
Task 4
4.1 There is a txt file on the desktop named file.txt. Using one of the three discussed tools in this task, what is the text within the ADS?
Open a cmd and type in the following
cd desktop
stream file.txt
notice there is an ads.txt inside
type in notepad file.txt:ads.txt
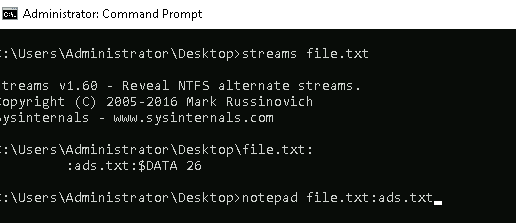
Answer: I am hiding in the stream.
Task 5
Read all that is in this task
5.1 Using WHOIS tools, what is the ISP/Organization for the remote address in the screenshots above?
whois -v <IP>
It is not giving any result but navigating to the below website we see the organization. For whois is best to use online tools
52.154.170.73 IP Address Whois | DomainTools.com
Answer: Microsoft Corporation
Task 6
Read all that is in this task and start autoruns and click on the Image Hijacks tab
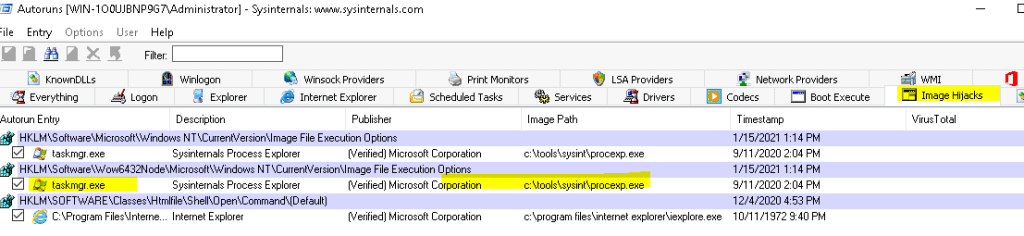
6.1 What entry was updated?
Answer: taskmgr.exe
6.2 What entry was updated?
Answer: c:\tools\sysint\procexp.exe
Task 7
Read all that is in this task and press complete
Task 8
Read all that is in this task and press complete
Task 9
Read all that is in the task
9.1 Run the Strings tool on ZoomIt.exe. What is the full path to the .pdb file?
Type in the following command
strings .\zoomit.exe | findstr /i .pdb
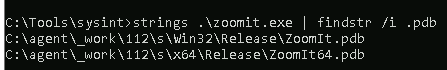
Answer: C:\agent_work\112\s\Win32\Release\ZoomIt.pdb
Task 10
Read all that is in this task and press complete











