This is the write up for the room Wireshark 101 on Tryhackme and it is part of the Tryhackme Cyber Defense Path
Make connection with VPN or use the attackbox on Tryhackme site to connect to the Tryhackme lab environment
Tasks Wireshark 101
Task 1
Read all that is in this task and press complete to continue
Task 2
If you are using kali then you are good to go if not then install Wireshark
apt install wireshark
Press complete when done
Task 3
To start Wireshark type in the following command
Wireshark
You can also find it in the start menu in Kali
Read all that is in this task. Play around with the menus and various features of Wireshark to get a feel for it, some of the features we will be going into further detail within later tasks.
Task 4
Read all that is in this task and press complete
Task 5
Filtering Operators we need to know
Wireshark only has a few that you will need to be familiar with:
- and – operator: and / &&
- or – operator: or / ||
- equals – operator: eq / ==
- not equal – operator: ne / !=
- greater than – operator: gt / >
- less than – operator: lt / <
Press complete when you have read all that is in this task
Task 6
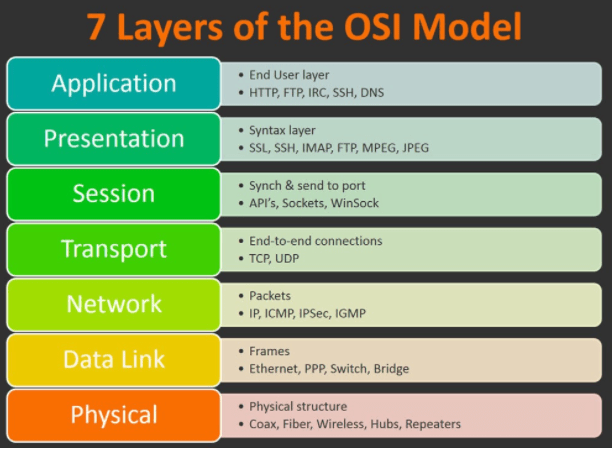
Read all that is in this task and press complete
Task 7
Download the PCAP wile attached to this task and open it in Wireshark
7.1 What is the Opcode for Packet 6?
Select packet 6
Open Address Resolution Protocol and select Opcode
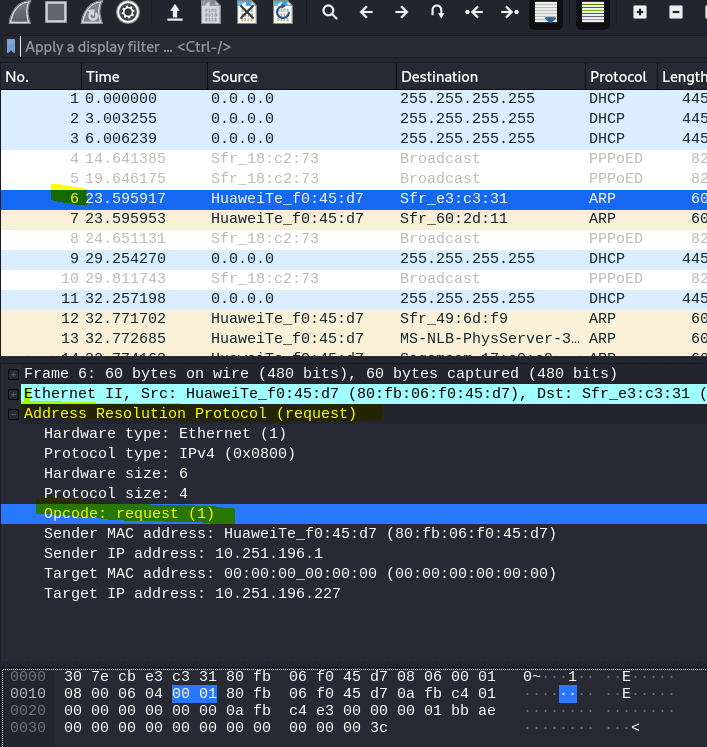
Answer: Request (1)
7.2 What is the source MAC Address of Packet 19?
Select packet 19
You can find it in 2 places
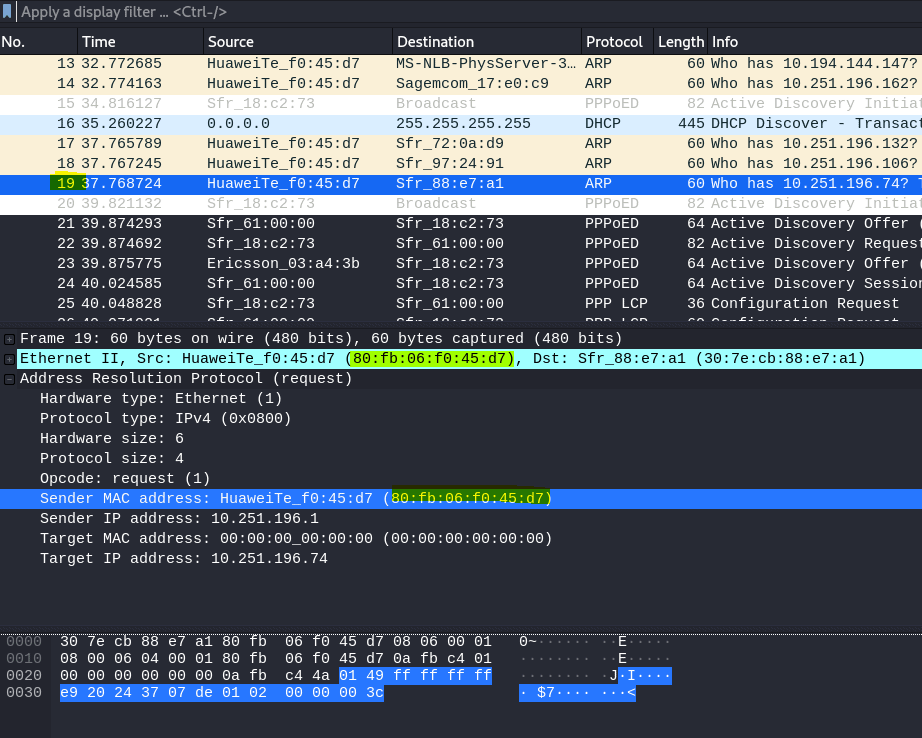
Answer: Correct Answer
7.3 What 4 packets are Reply packets?
First we need to filter the arp protocol.
Type in the filer box
arp
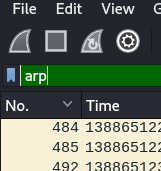
Now scroll down till you see a packet wich has a diffrent info
The open that packet and open up the address Resolution Protocol and the the opcode. Rigth click the opcode and select apply as filter and the selected
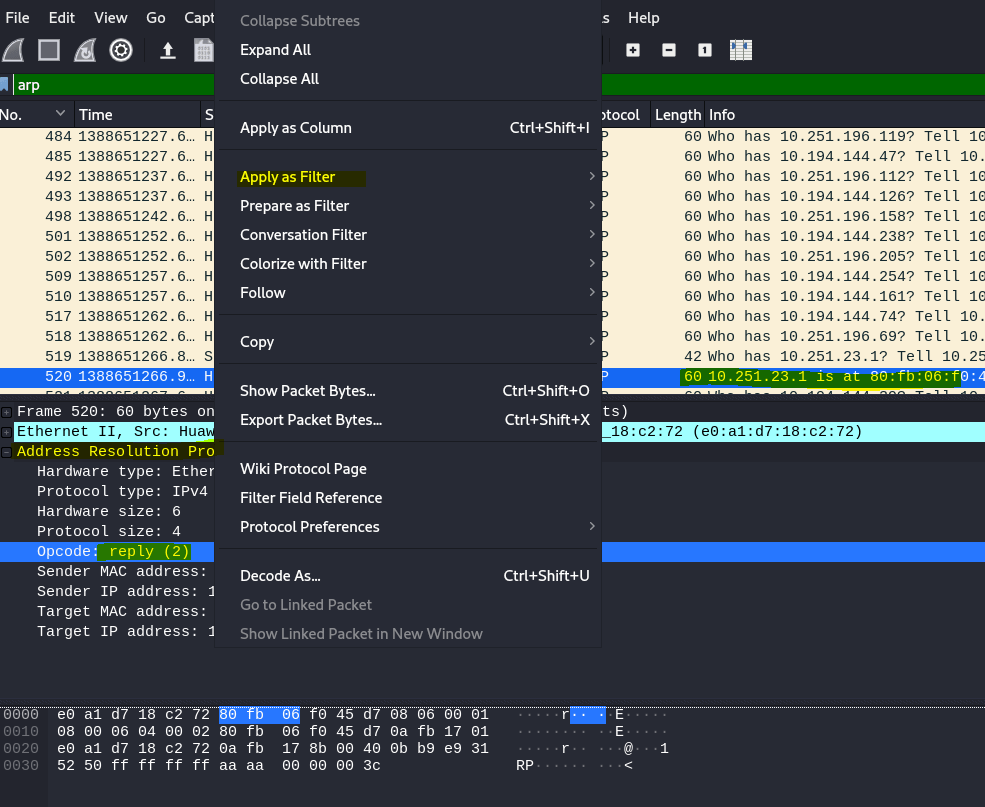
It will now filter all the reply packats
Notice the filter code change to arp.opcode == 2
This is the direct filter code but I just wanted to show you how you can filter with some clicks as well
Answer
7.4 What IP Address is at 80:fb:06:f0:45:d7?
You can see it in the filter from previous task.
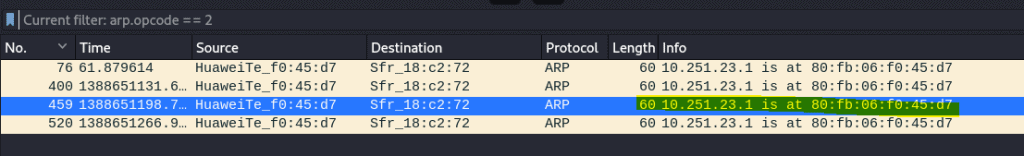
Answer: 10.251.23.1
Task 8
Download the PCAP file attached to this task and open it
8.1 What is the type for packet 4?
Select packet 4
Open Internet Control Message Protocol
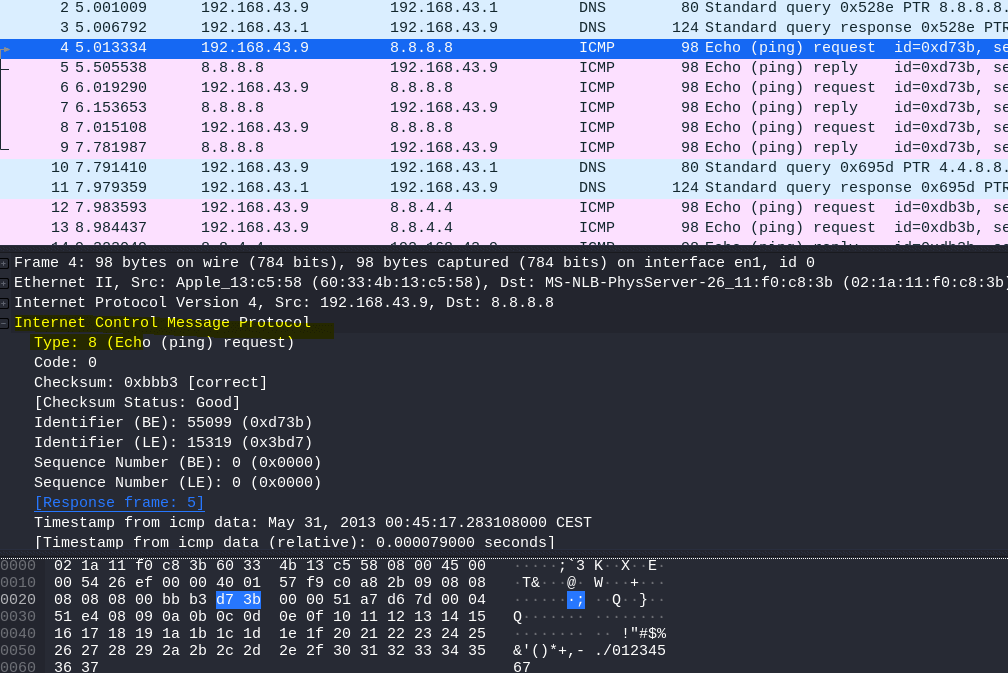
Answer: 8
8.2 What is the type for packet 5?
Select packet 5
Open Internet Control Message Protocol
Answer: 0
8.3 What is the timestamp for packet 12, only including month day and year?
Select packet 12
Open the frame
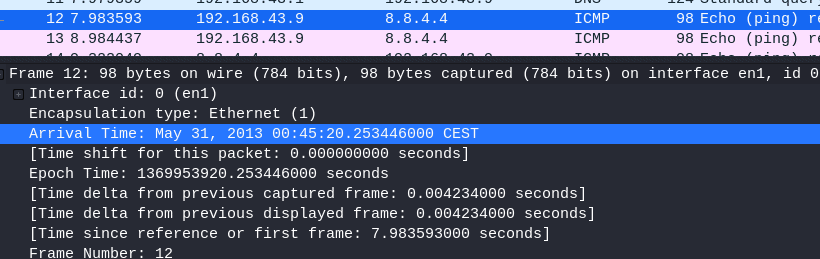
note: Wireshark bases it’s time off of your devices time zone, if your answer is wrong try one day more or less.
Because of the time frame I’m in my answer is
May 30, 2013
8.4 What is the full data string for packet 18?
Select packet 18
Open internet control Message
Open data
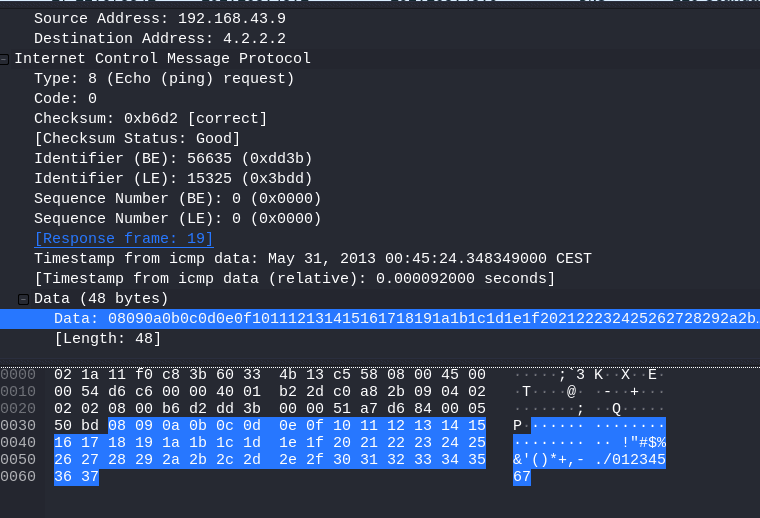
Answer: 08090a0b0c0d0e0f101112131415161718191a1b1c1d1e1f202122232425262728292a2b2c2d2e2f3031323334353637
Task 9
Read all that is in the task and press complete
Task 10
Download the PCAP file attached to this task and open it with Wireshark
10.1 What is being queried in packet 1?
Select Packet 1
Open Domain Name System
Open Queries
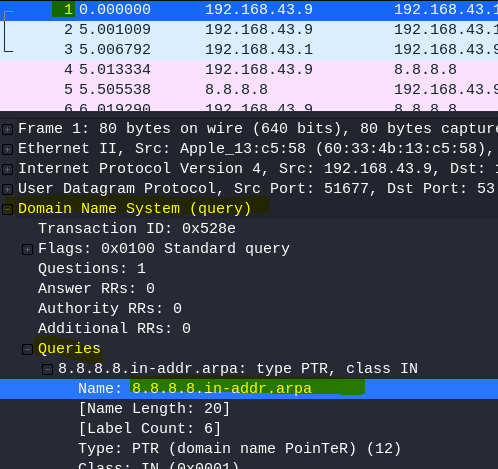
Answer: 8.8.8.8.in-addr.arpa
10.2 What site is being queried in packet 26?
Select Packet 26
Open Domain Name System
Open Queries
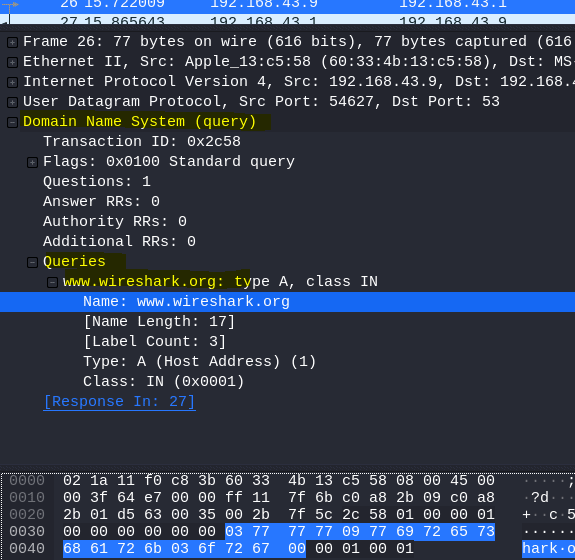
Answer: www.wireshark.org
10.3 What is the Transaction ID for packet 26?
You can fnd this in the screenshot of previous task
Answer: 0x2c58
Task 11
Download the PCAP file attached to this task and open it with Wireshark
11.1 What percent of packets originate from Domain Name System?
Navigate to Statistics > Protocol Hierarchy.
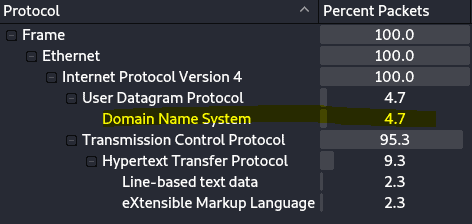
Answer: 4.7
11.2 What endpoint ends in .237?
Just look at the second packet. It is already in the destination field
Answer: 145.254.160.237
11.3 What is the user-agent listed in packet 4?
Select Packet 4
Open Hypertext Transfer Protocol
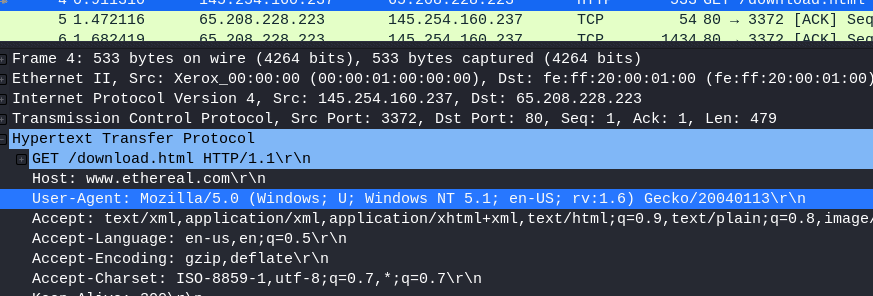
Answer: Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; rv:1.6) Gecko/20040113
11.4 Looking at the data stream what is the full request URI from packet 18?
Select packet 18
Open Hypertext Transfer Protocol
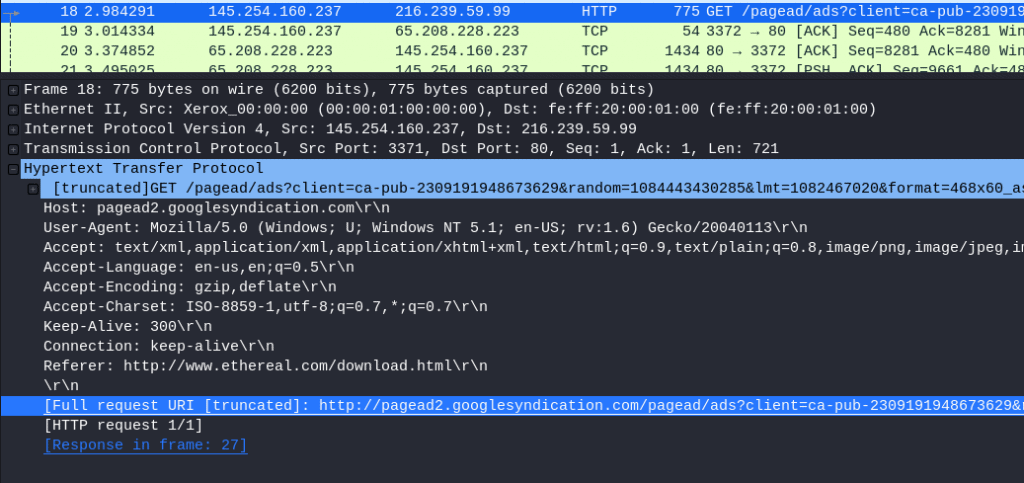
Answer: http://pagead2.googlesyndication.com/pagead/ads?client=ca-pub-2309191948673629&random=108
11.5 What domain name was requested from packet 38?
Select packet 38
Select the Hyper Text Protocol
Answer: www.ethereal.com
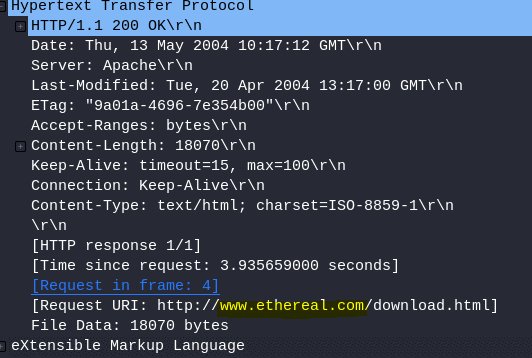
11.6 Looking at the data stream what is the full request URI from packet 38?
The answer is in the previous screenshot at the same location
Answer: http://www.ethereal.com/download.html
Task 12
The task is a littl eoutdated with the wireshark version I have. We use TLS as protocol for the decryption
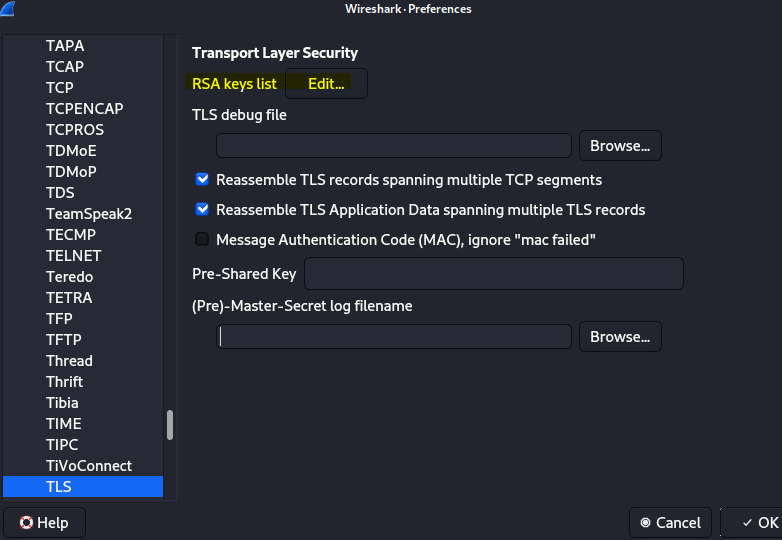
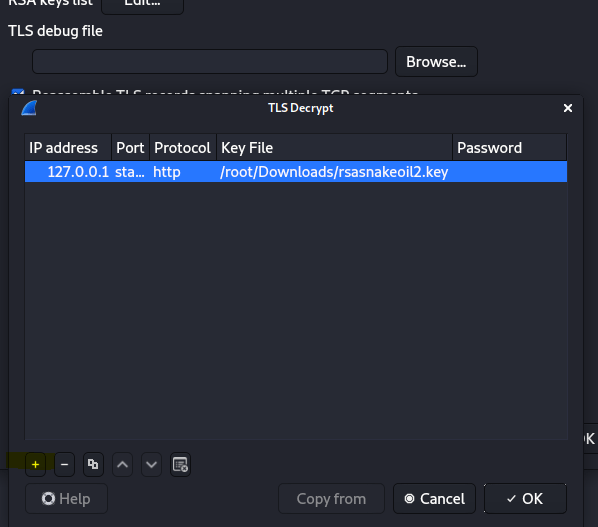
12.1 Looking at the data stream what is the full request URI for packet 31?
Select Packet 31
Open Hypertext Transfer Protocol
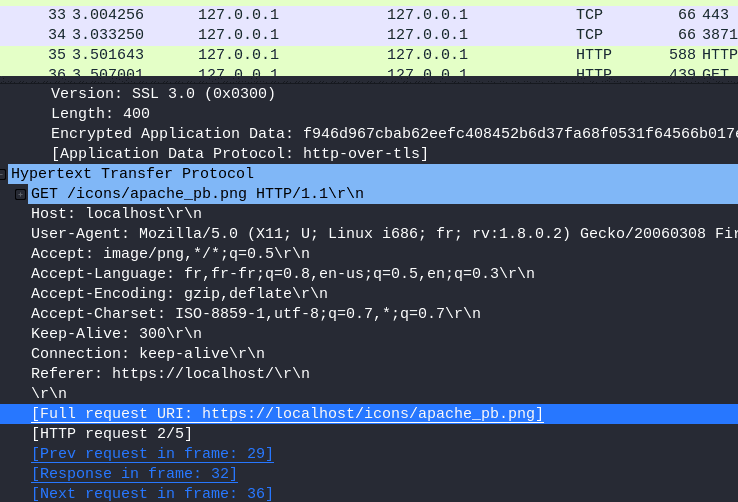
Answer: https://localhost/icons/apache_pb.png
12.2 Looking at the data stream what is the full request URI for packet 50?
Select Packet 50
Open Hypertext Transfer Protocol
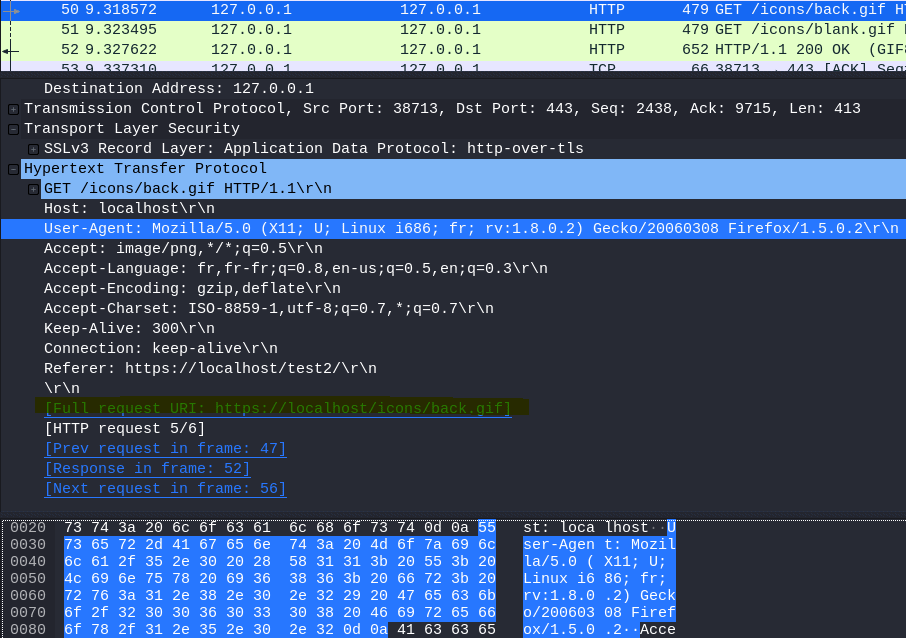
Answer: https://localhost/icons/back.gif
12.3 What is the User-Agent listed in packet 50?
Select Packet 50
Open Hypertext Transfer Protocol
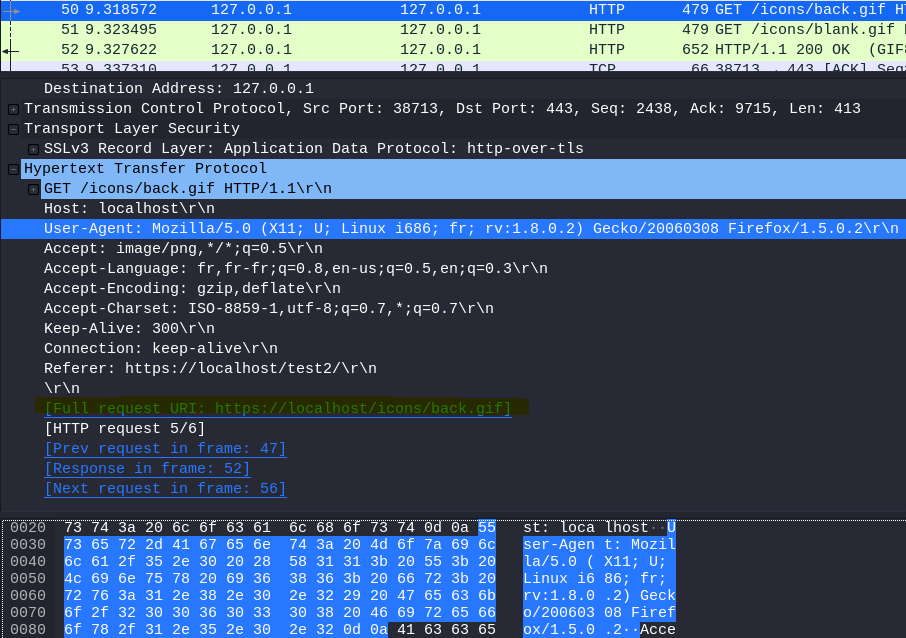
Answer: Mozilla/5.0 (X11; U; Linux i686; fr; rv:1.8.0.2) Gecko/20060308 Firefox/1.5.0.2
Task 13
Read all that is in the task, Follow along and press complete
Task 14
Read all that is in the task and press complete
And this conclude the guide of the Wireshark 101 room on tryhackme











