This is the write up for the room Linux Fundamentals part 3 on Tryhackme and it is part of the complete beginners path
Make a connection with VPN or use the attack box on Tryhackme site to connect to the Tryhackme lab environment.
Tasks Linux Fundamentals Part 3
Task 1
Read all that is in the task and press complete
Task 2
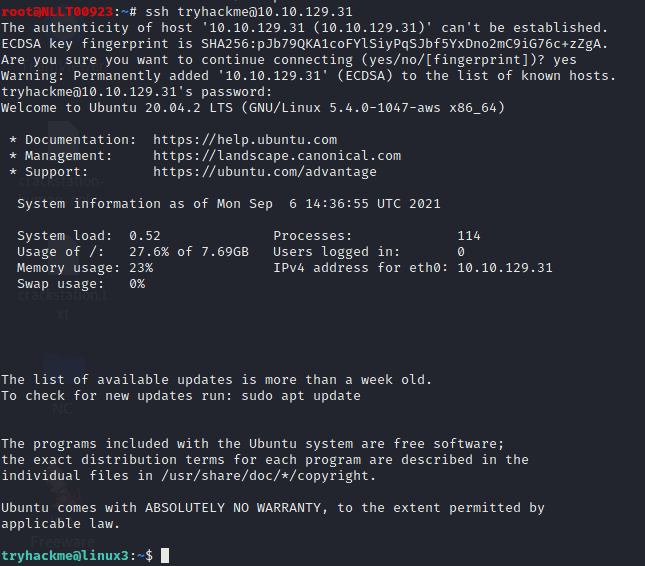
Start the machine attached to this task then connect with it over ssh or use the attack box with the credentials given in the task then press complete.
Task 3
To create a file with nano just type
nano filename
3.1 Edit “task3” located in “tryhackme”‘s home directory using Nano. What is the flag?
Type in the command
nano task 3
The flag will reveal itself
Task 4
Type in the following command to start a python webserver on the default port
python3 -m http.server
now open a second terminal so we can copy the file over.
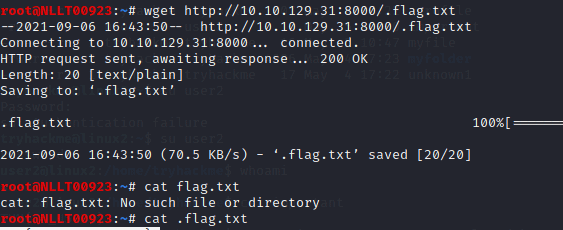
Type in the following command
wget HTTP://<MACHIEN_IP>:8000/.flag.txt
Once the file is copied over you can cat the output to the screen
cat .flag.txt
Task 5
Read all that is in this task and learn about the differences
5.1 If we were to launch a process where the previous ID was “300”, what would the ID of this new process be?
Answer: 301
5.2 If we wanted to cleanly kill a process, what signal would we send it?
Answer: SIGTERM
5.3 Locate the process that is running on the deployed instance (10.10.129.31). What flag is given?
Type in the following command
ps aux
The answer is in the output starting with THM
5.4 What command would we use to stop the service “myservice”?
Answer: systemctl stop myservice
5.5 What command would we use to start the same service on the boot-up of the system?
Answer: systemctl enable myservice
5.6 What command would we use to bring a previously backgrounded process back to the foreground?
Answer: fg
Task 6
6.1 When will the crontab on the deployed instance (10.10.129.31) run?
To find the answer we need to take a look inside the crontab by typing the following command
crontab -a
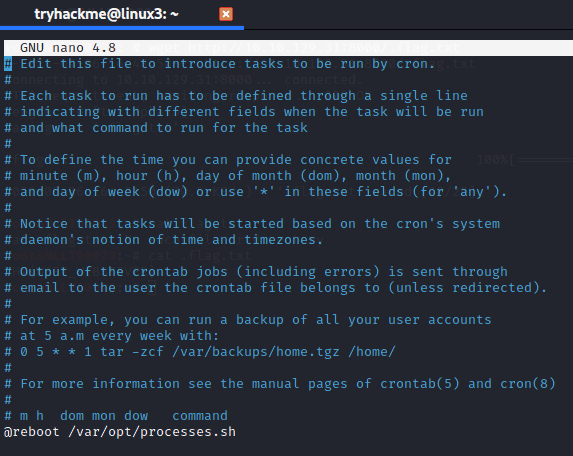
Answer: @reboot
Task 7
Read all that is in this task and press complete
Task 8
Navigate to the login of apache by typing gin the following command
cd /var/log/apache2
8.1 What is the IP address of the user who visited the site?
type in the following command to cat out the correct logging
cat access.log.1
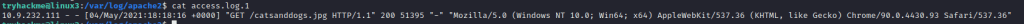
8.2 What file did they access?
Answer: catsanddogs.jpg
Task 9
Read all that is in the task and press complete