This is the write up for the room Nmap on Tryhackme
Make connection with VPN or use the attackbox on Tryhackme site to connect to the Tryhackme lab enviroment
Tasks
Task 1:
Press on deploy to deploy the VM connected to this room after reading the task. Press complete to move to Task 2
Task 2:
Read all that is in the task.
Question one and two can be found in the text of the task itself
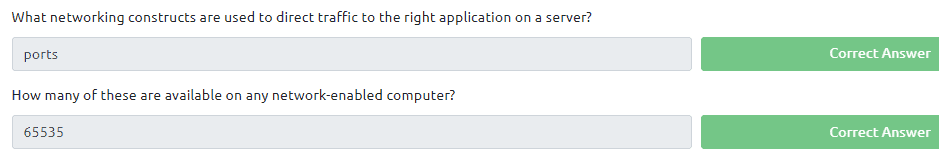
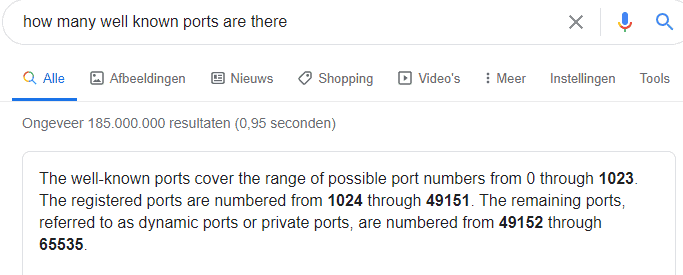
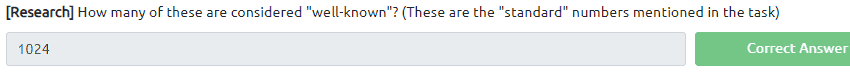
Question 3 can be found with a good google string and remember 0 is also a port
Task 3:
Read all that is in the task. All the question answers can be found with either the command man nmap or nmap -h . There are 15 questions in this task. Let’s get started
3.1 Type in the command nmap -h
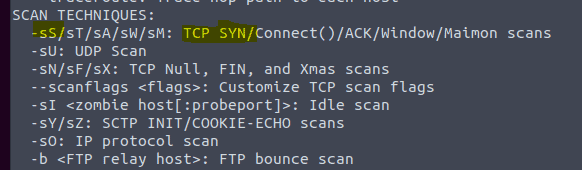
3.2 Type in the command nmap -h
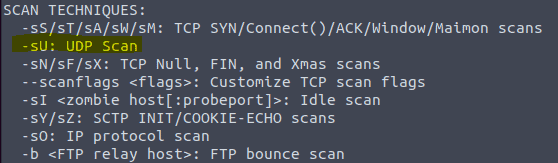
3.3 Type in the command nmap -h
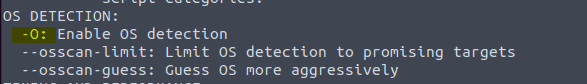
3.4 Type in the command nmap -h
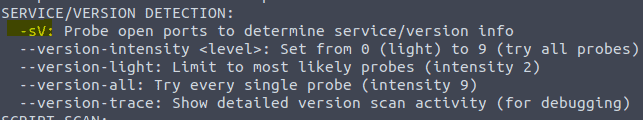
3.5 and 3.6 Type in the command nmap -h
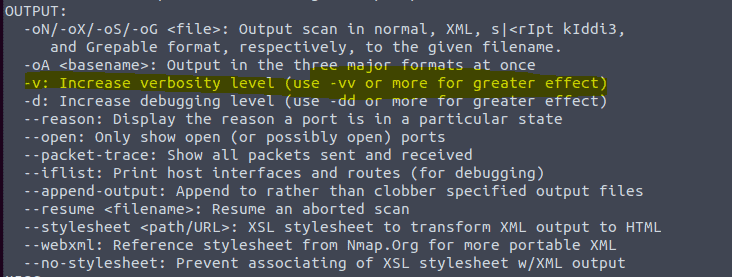
3.7 Type in the command nmap -h
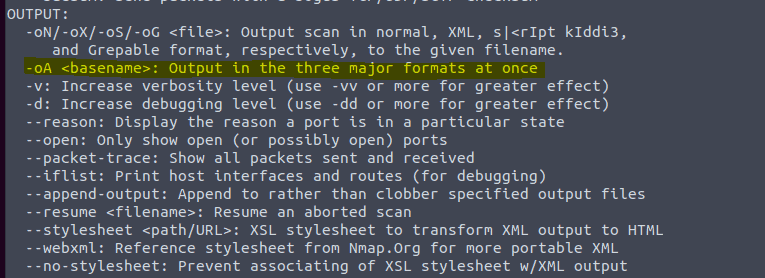
3.8 and 3.9 Type in the command nmap -h
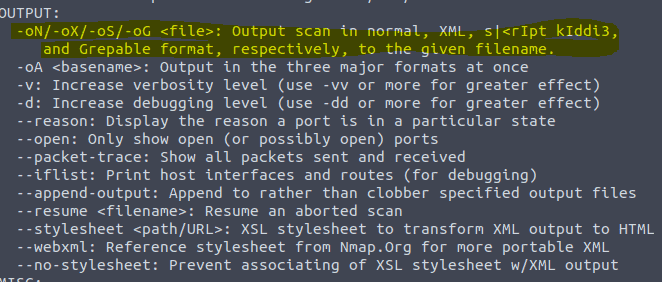
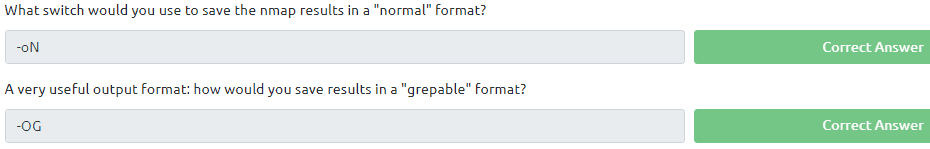
3.10 his one took me a while to find but it is under the same help page. Type in the command nmap -h
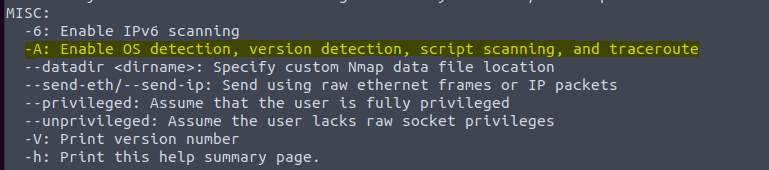
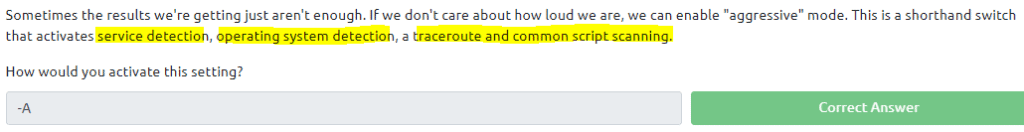
3.11 , 3.12 and 3.13 Type in the command nmap -h
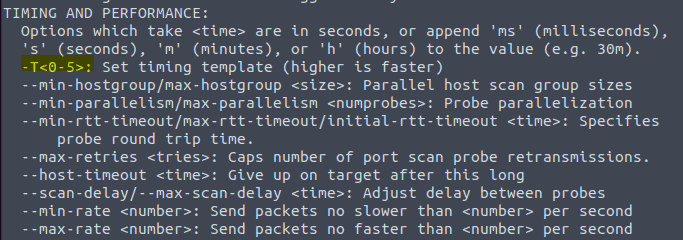
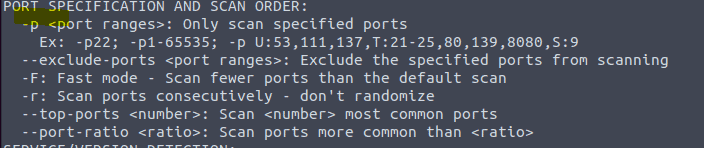
3.14 Type in the command man nmap
The script engine explanation will be after line 1222
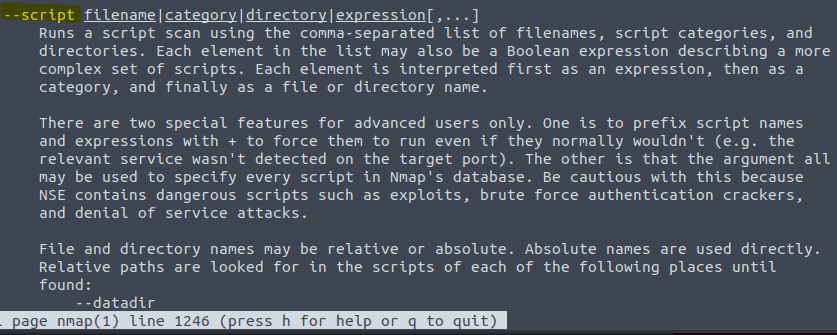
3.15 Type in the command nmap -h
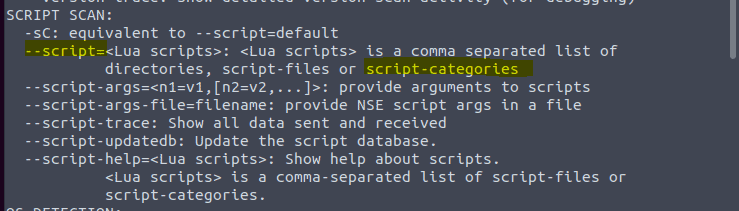
Scan Types
Task 4:
Read all that is in the task and press complete
Task 5:
The answer of these question can be found it the task. Just by reading the task you can answer these questions
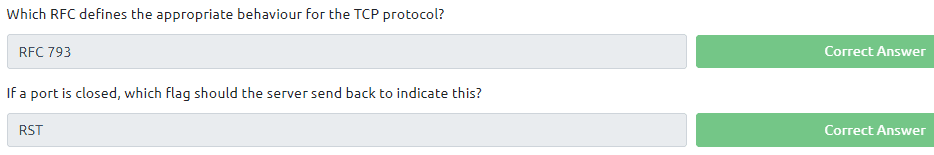
Task 6:
Read all that is in the task. The answers of the questions in these task can be found in the text of this task
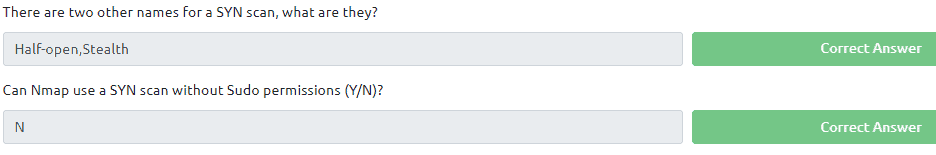
Task 7:
Read all that is in the task. The answers of the questions in these task can be found in the text of this task
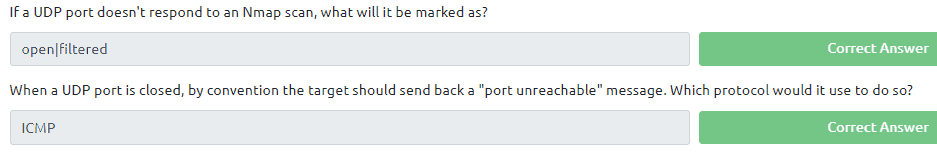
Task 8:
Read all that is in the task. The answers of the questions in these task can be found in the text of this task
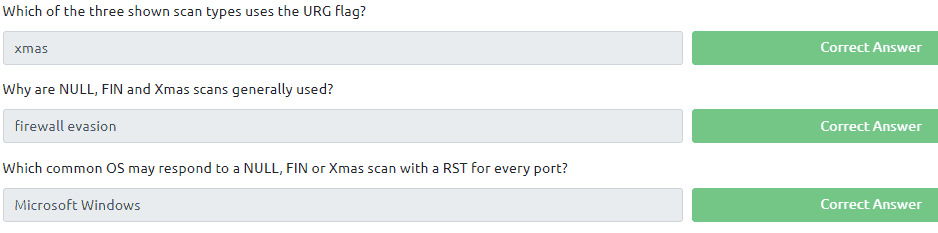
Task 9:
Read all that is in the task. The task is learning you about the parameter -sn. As for subnet 255.255.0.0 it is a class B network also stated under the hint button. So the answer to this question nmap -sn 172.16.0.0/16
NSE Scripts
Task 10:
Read all that is in the task. The answers of the questions in these task can be found in the text of this task. As for the last question in this task. Just think about what you do not want in an production environment.
Task 11:
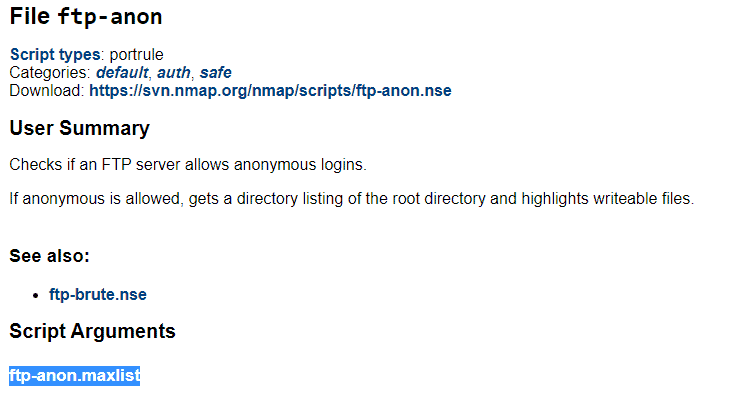
Read all that is in the task. For th firt question open the link that is provided in the task NSEDoc Reference Portal
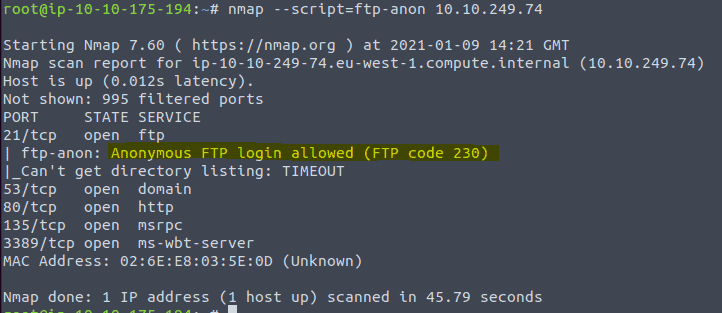
Search for ftp-anon
Task 12:
For the first question type cd /usr/share/nmap/scripts in the terminal and press enter. The type ls smb* in the terminal and press enter. Firs command is to naviagte to the right directory as stated in the task and the second shows all files that start with smb. If you do not know these command then please start with the Linux Fundamentals Part 1
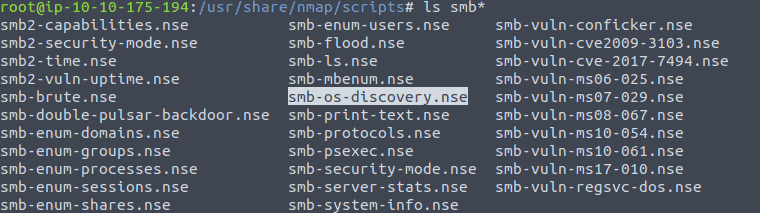
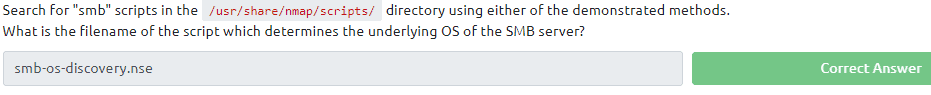
For the second question we need to cat the the script to screen by entering the following command cat smb-os-discovery.nse
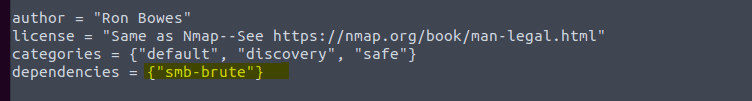
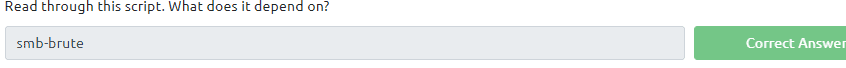
Task 13:
Read all that is in the task. The answer of the first question can be found in the text of the task. And knowing what te ping protocol is. Which was already cover earlier in this room
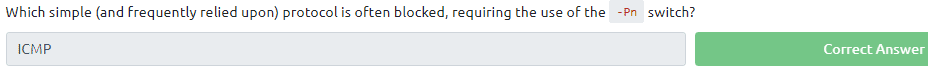
For the next question type in the command nmap -h
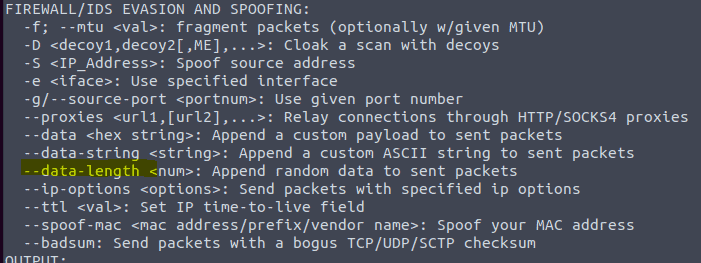
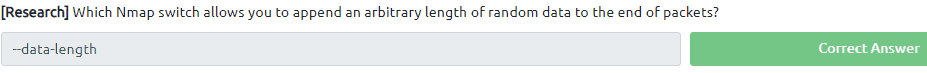
The Practice part for nmap
Task 14:
Now we are going to use the machine we spinned up in the beginning of the room.
14.1 Type in the command ping <IP of the VM> With Control+C you can stop the ping command
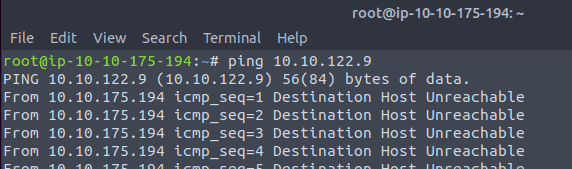
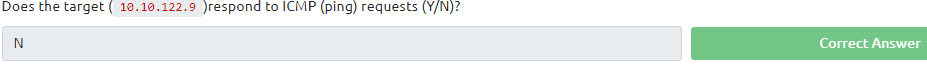
14.2 Type in the command nmap -sX -Pn <IP of VM>
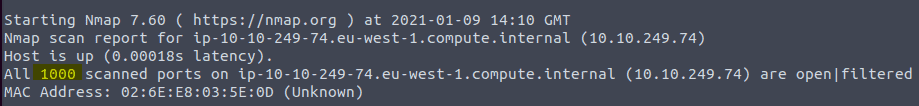
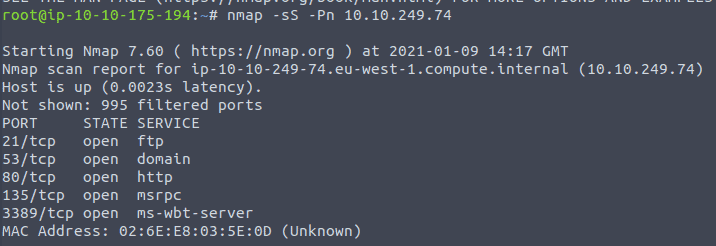
The question is asking for the first 999 ports. 1000 are open
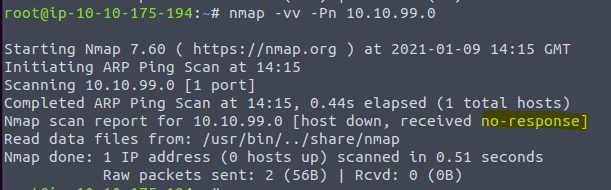
14.3 The asnwer of the third question can be found in the hint. Type in the command nmap -vv -Pn <ip of vm>
14.4 type in the command nmap -sS -Pn <IP of VM>
For the last question type in the parameters –script=ftp-anon <IP of VM>
Task 15:
Read all of the task and press complete
Conclusion of the Room Nmap on tryhackme
We now know what the scanning tool to use. It is allot to take in and will only remember most of it by just using it. Practice is key.
I know there are tons of resource on the internet about this tool. This room learned me a couple new things like using scripts and still scanning a machine even if there is no ping request back but you know it is onlne