This is the write up for the room ZTH – Web 2 on Tryhackme and it is part of the Web Fundamentals Path
Make connection with VPN or use the attackbox on Tryhackme site to connect to the Tryhackme lab environment
TASK ZTH – Web 2
Task 1
Read all that is in the task and start up the Machine attached to this task
Task 2
Read all that is in the task and press complete
Task 3
If you have started the machine then navigate to http://MACHINE_IP
You can follow along with the task. The credentials needed are in the next task
Press complete when done
Task 4
4.1 What is the flag
Think about the ID of the first user
Type in
http://MACHINE_ID/note.php?note=0
The answer will be on this page
Task 5
Read all that is in this task and press complete
Task 6
Read all that is in the task and press complete
Task 7
7.1 What flag hides characters
Type in the following command
wfuzz -h
Answer: --hh
7.2 What flag shows specific word amounts instead of hides them
Type in the following command
wfuzz -h
Answer: --sw
Task 8
Navigate to http://ACHINE_IP:81 and log in with the provided credentials from task 6
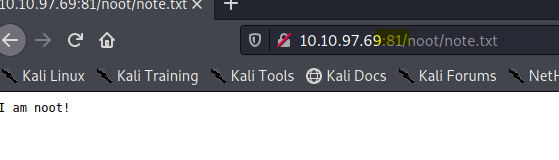
We have just learned how the fuzz. Note: the word FUZZ is where the program changes the word from the wordlist
Type in the following command
wfuzz -c -z file,/usr/share/wordlists/dirb/big.txt --hw 57 10.10.97.69:81/FUZZ/note.txt
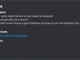
After a while you will find the correct user. Type that user in the URL instead of noot
http://MACHINE_IP:81/USERHERE/note.txt
Task 9
Read all that is in this task and press complete
Task 10
You can follow along with this task if you use port 82. So the URL will be
http://MACHINE_IP:82/
Login will be the same as previous tasks
When done press complete
Task 11
11.1 What is the flag
We do not need to login. If you are still logged in then http://10.10log out
Type in the terminal
dirbuster&
user this wordlist
/usr/share/wordlists/dirb/big.txt
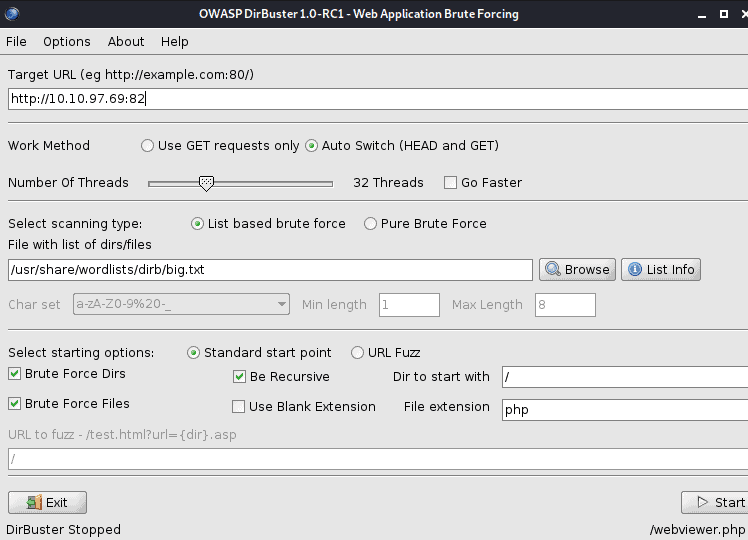
This is the way we will find the api.php
Now we need to fuzz it in order to get the parameter. We already know we are looking for flag.txt
Type in the following command
wfuzz -c -z file,/usr/share/wordlists/dirb/big.txt --hw 0 10.10.97.69:82/api.php?FUZZ=flag.txt
You will find a word go to the same link and change that worrd with the FUZZ
http://MACHINE_IP:82/api.php?FUZZ=flag.txt